The art of understanding data sensitivity
Introduction to Data Security

Angeline Corvaglia
Founder & Digital Transformation Specialist
Data sensitivity is of paramount importance
![]()
Sensitive data needs extra protection because of the risks associated with it falling into the wrong hands
It is about determining:
- What data needs to be protected
- Who should access it
- How to safeguard it best
The risks of mismanagement
- Data breaches
- Unauthorized access
- Compliance issues
- Reputation
- Customer trust
- Fines, legal fees, and lost customers
- Personally Identifiable Information (PII) can cause significant damage if in the wrong hands
![]()
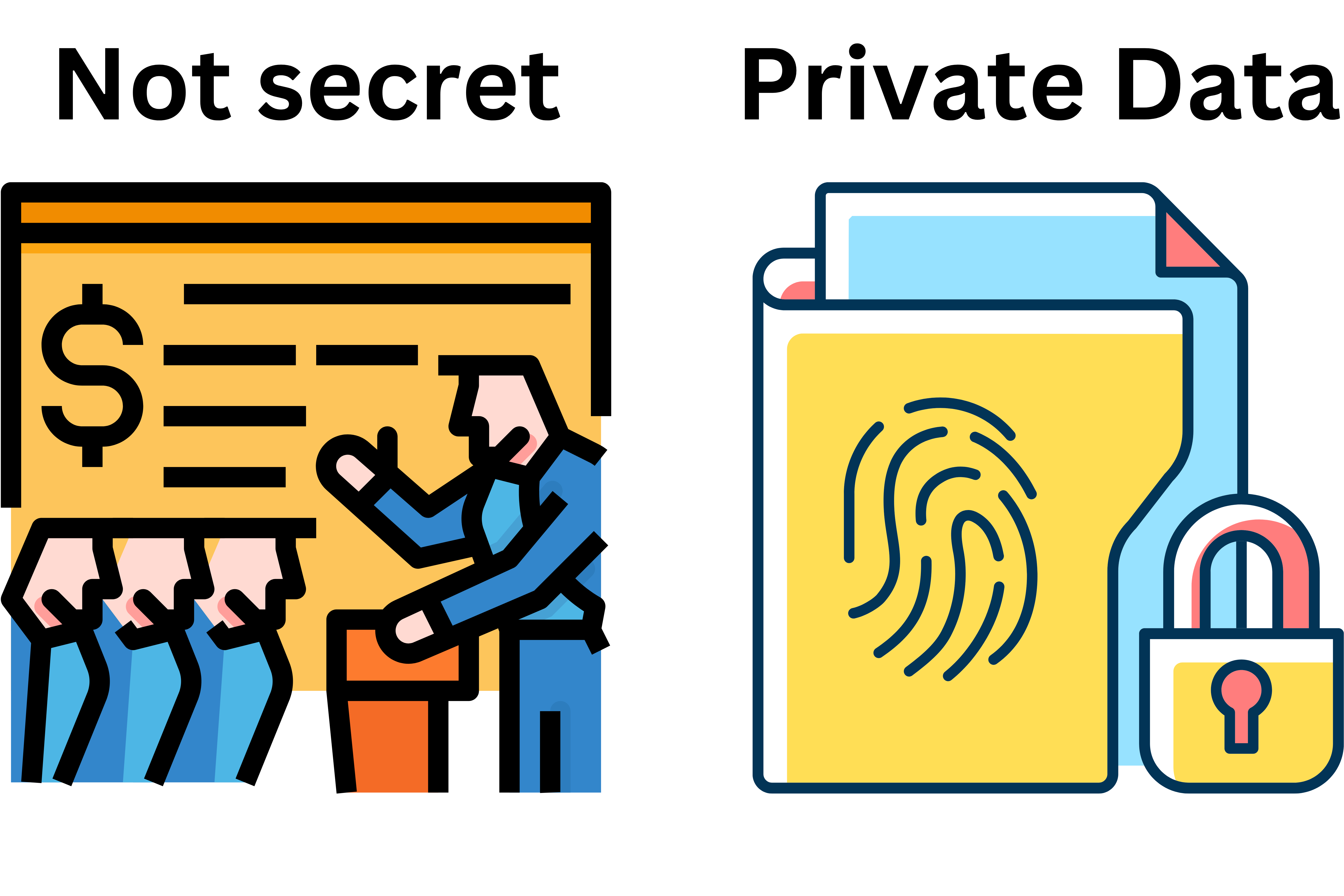
Public versus private data
Confidentiality, importance, and protection based on its potential impact
Group data by risk and impact
- Public
- Internal
- Confidential
- Top Secret
With each group, the level of sensitivity of the data increases

Public data
Generally accessible to anyone
No negative impact linked to people seeing it

- Public social media posts
- Website content
- Company press releases
Internal data
Only for employees or trusted partners of a company
Moderate negative potential impact if unauthorized people see it

- Meeting minutes
- Internal worker notes
- Company policies
Confidential data
Private and needs protection
Personally Identifiable Information (PII)

- Customer phone numbers
- Personal bank account numbers
- Private strategic plans
Top-secret data
Highly confidential
Significant damage to a company if unauthorized persons access it

- Scientific research
- Government intelligence
- Sensitive personal information such as US Social Security numbers
What everyone should know

- Their company's data classification levels
- Who should be able to access each level
- Rules for putting data into each group
- What counts as PII
- How to handle data based on sensitivity levels
- Process for reporting potential data breaches
Real-life consequences at Equifax
Exposed the Personally Identifiable Information (PII) of 147 million people

Significant cost and reputational damage
- $1.4 billion for technology infrastructure cleanup and security improvement
- Over $400 million in fines
Let's practice!
Introduction to Data Security

