Top data protection strategies
Introduction to Data Security

Angeline Corvaglia
Founder & Digital Transformation Specialist
What are data protections measures?
Wide range of strategies, techniques, and tools
Prevent sensitive information from being:
- Accessed
- Altered
- Disclosed
- Destroyed by unauthorized parties
Ensure the confidentiality, integrity and availability of data

A comprehensive data security ecosystem
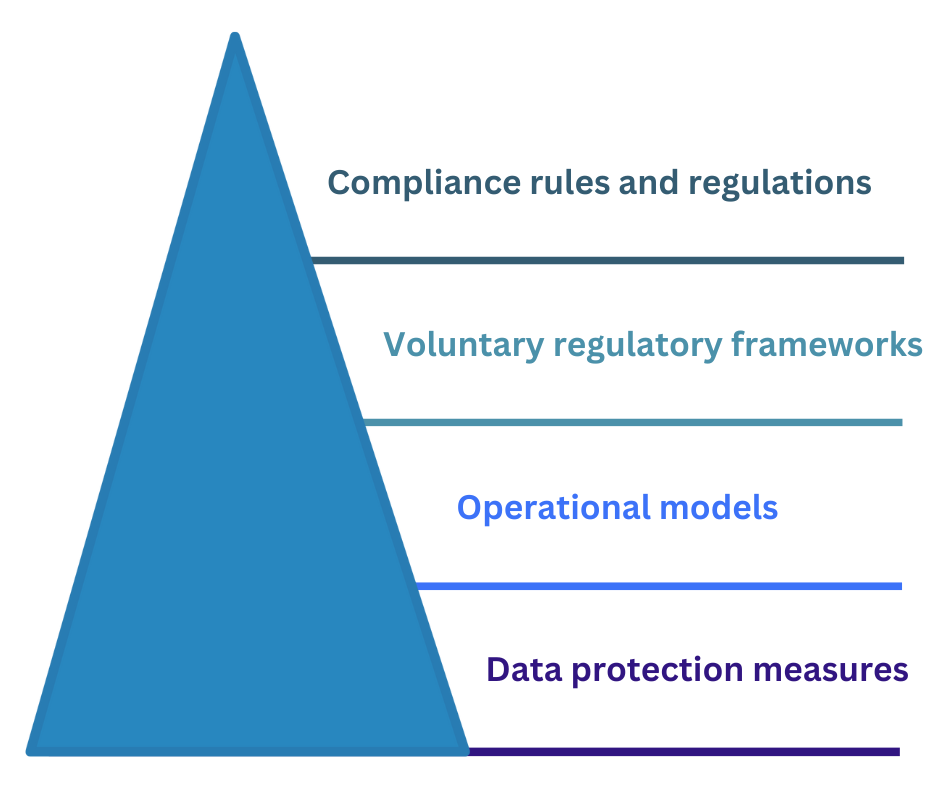
Fundamental data protection measures
![]()
Access controls: guarding the gates
![]()
First line of defense
- Determine who can enter, modify, or view specific resources
Examples:
- Strong password policies
- Multi-factor authentication
- Regular access reviews
Data encryption: transforming secrets
![]()
Transforms data
- Unusable even if unauthorized access occurs
Examples:
- Full disk encryption on data at rest
- Encrypting data in transit
- Carefully managing encryption keys
Hardware risks: taming the beasts within
![]()
If not managed properly, it can pose significant risks
Key elements to reduce risk:
- Maintaining an updated inventory of hardware assets
- Ensuring the physical safety of devices
- Updating firmware regularly
- Securely disposing of hardware
Cloud computing: navigating the skies safely
![]()
Presents unique security challenges with its distributed nature
Carefully select a cloud provider with:
- Robust security
- Encryption
- Industry-standard adherence
- Cloud Data Loss Prevention
Generative AI: a whole new challenge

Data protection strategies must evolve to address these risks
- Unintentional sensitive data sharing
- Unauthorized access to sensitive data
Let's practice!
Introduction to Data Security

