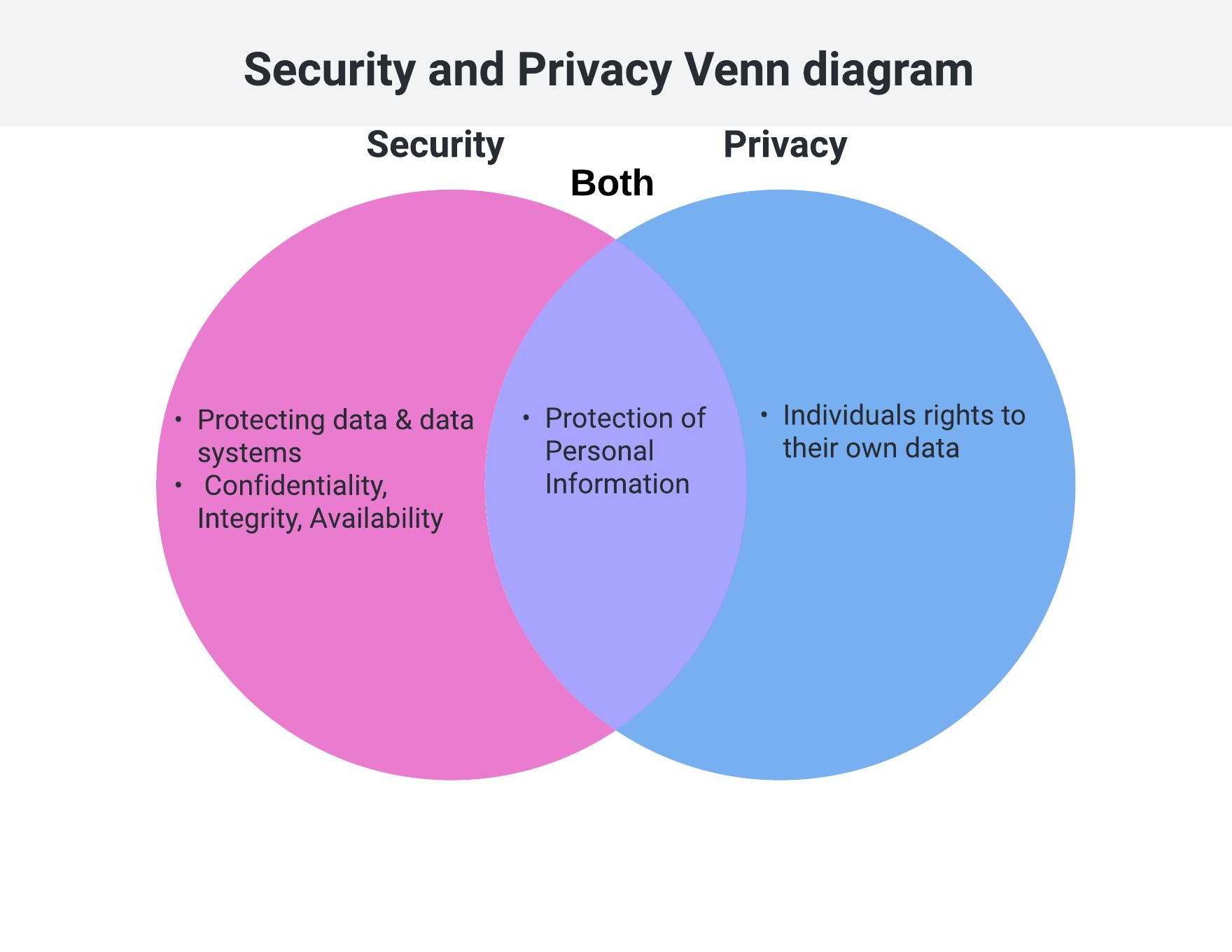
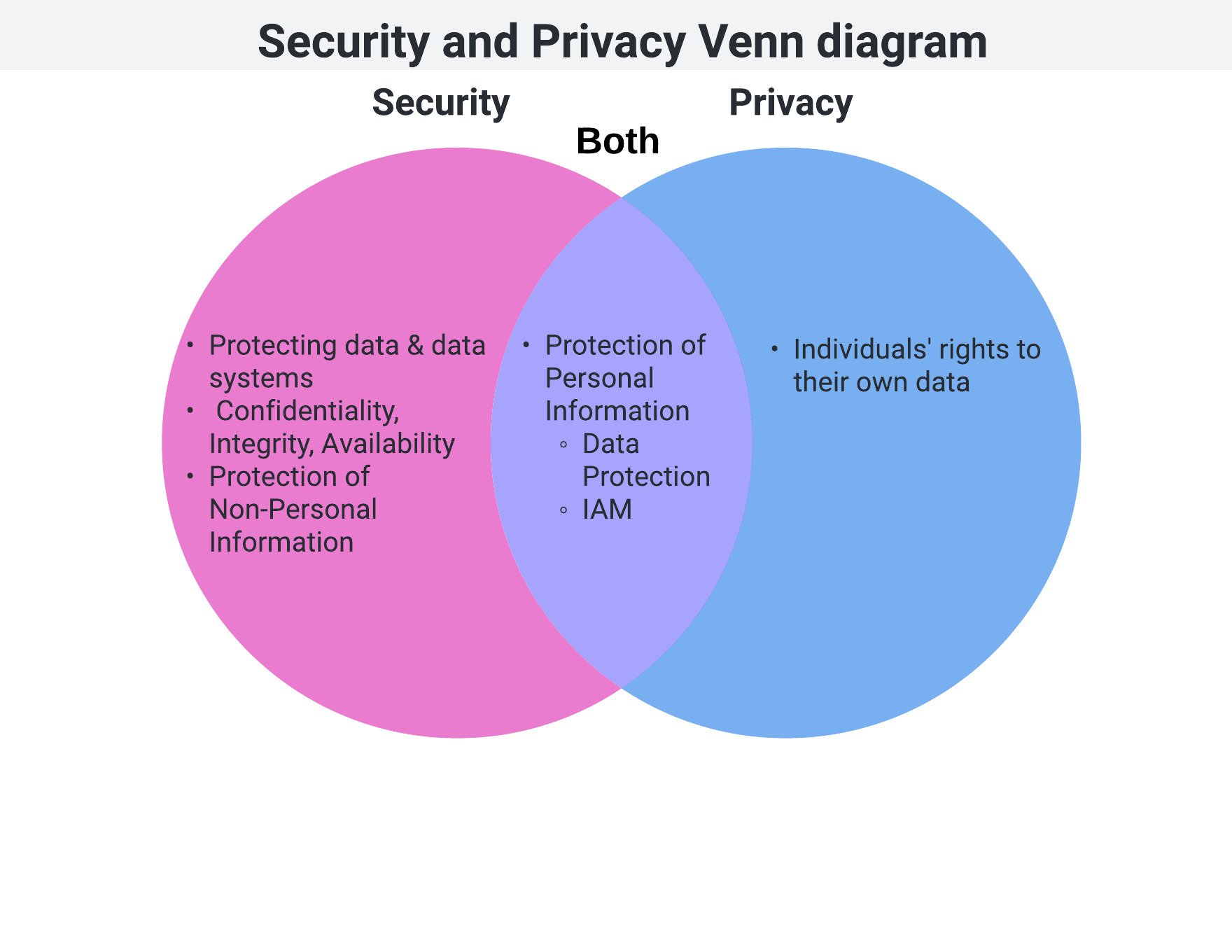
The relationship between Security and Privacy
Introduction to Data Privacy

Tiffany Lewis
Security and Privacy Instructor
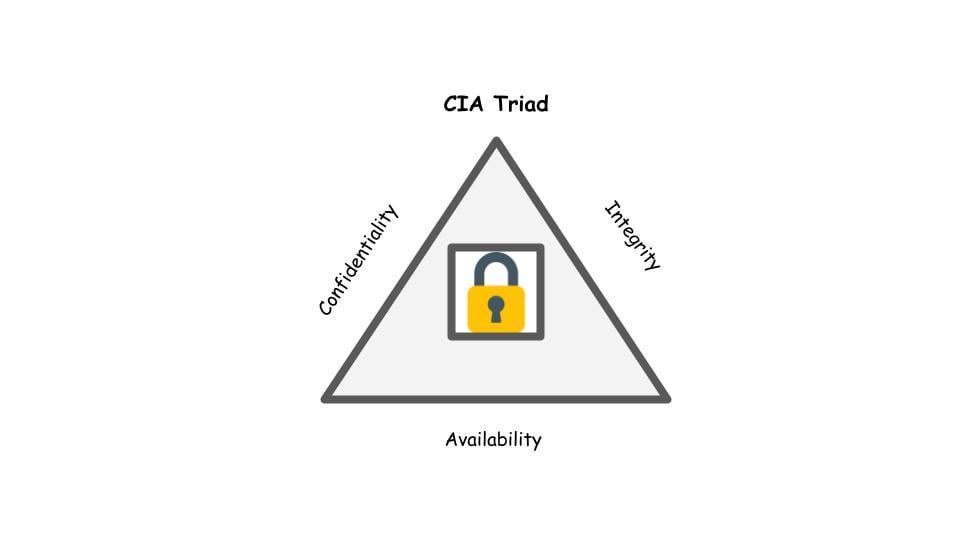
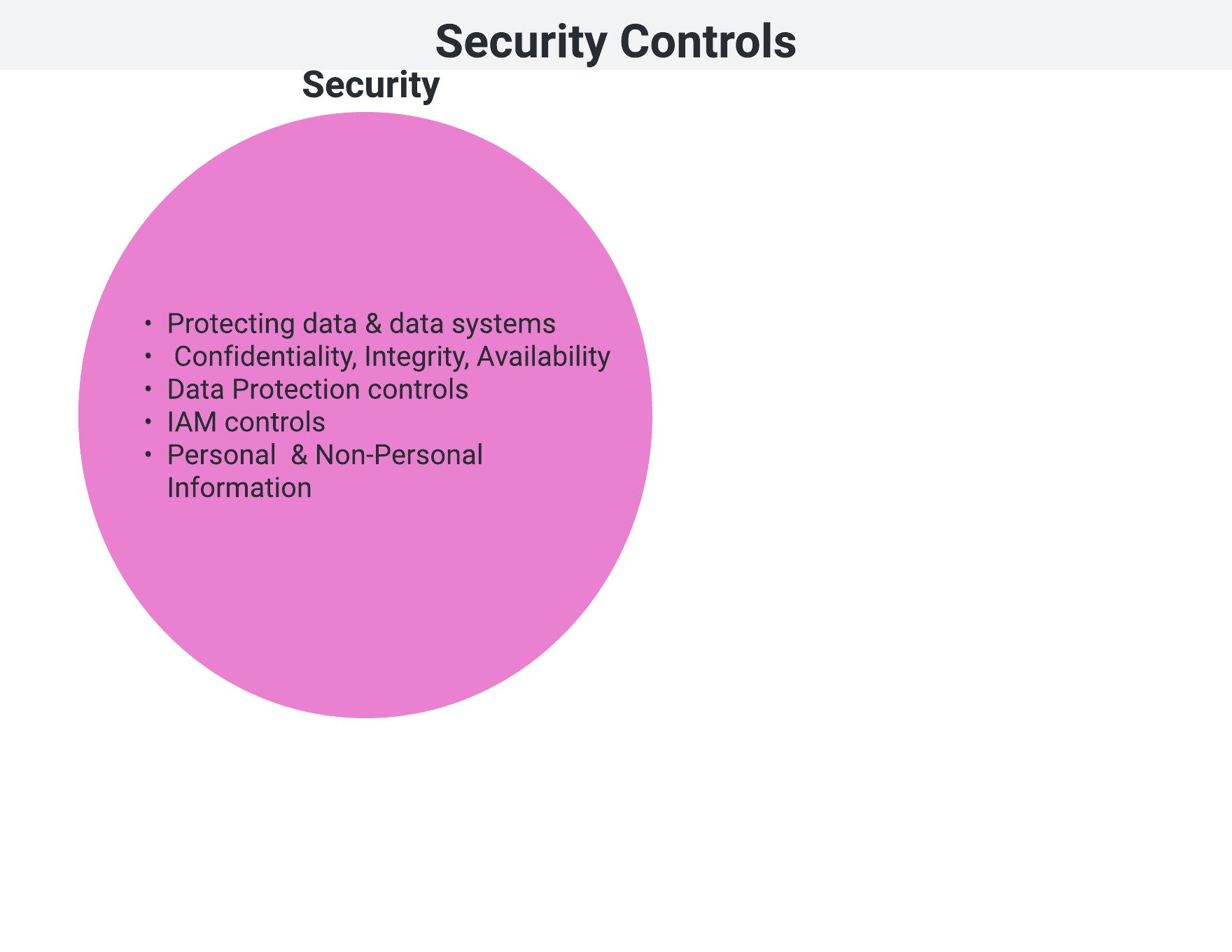
Security fundamentals
- Preventing unauthorized use, disclosure, and alteration of data:
- CIA Triad
- Examples:
- Encryption
- Identity Access Management
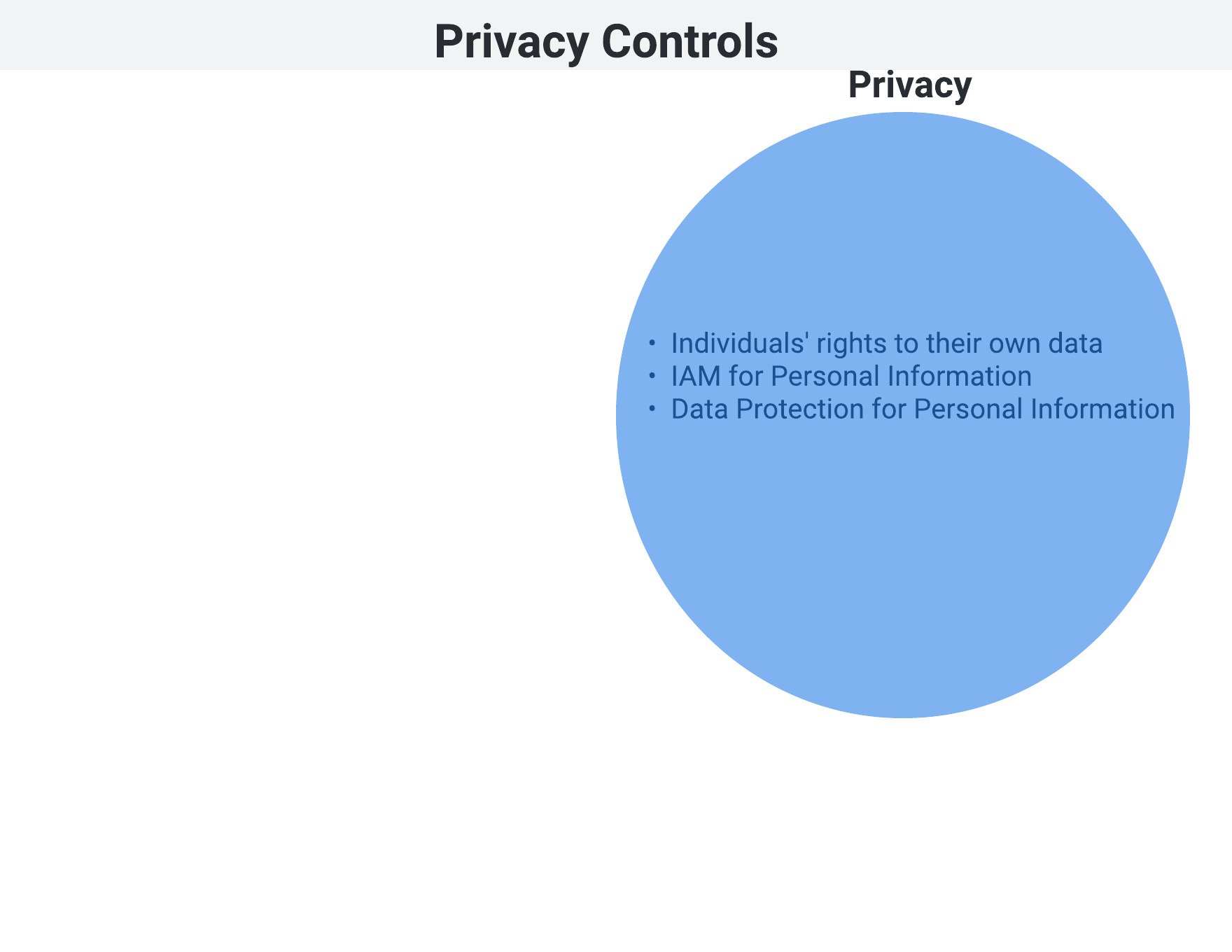
Privacy fundamentals
- Data processed in a valid manner that has been authorized by the user
- Examples:
- Notifications
- Encryption

Packing what we've learned
- Backpack startup
- Security and Privacy concerns
- Analyze:
- Product data
- Personal information

Security and Privacy failure
- Privacy requires explicit authorization from users to:
- disclose
- alter
- change how data is used
- Stolen data - no consent or authorization from users

Data breach
Data Breach - a security event where data is unlawfully disclosed, altered, or taken by an unauthorized party.
- Example: Yahoo data breach in 2013
- Affected over 3 billion users
- Hackers attempted to sell the data

1 https://www.nytimes.com/2017/10/03/technology/yahoo-hack-3-billion-users.html
Let's practice!
Introduction to Data Privacy

