De-Identifying data
Introduction to Data Privacy

Tiffany Lewis
Security and Privacy Instructor
Protecting sensitive information
- Protecting sensitive information
- Internal employees
- External actors
- Compliance implications
- Several layers of security

De-identification techniques
- Anonymization and pseudonymization
- Methods and tools used to make data unreadable
- Different use cases for each

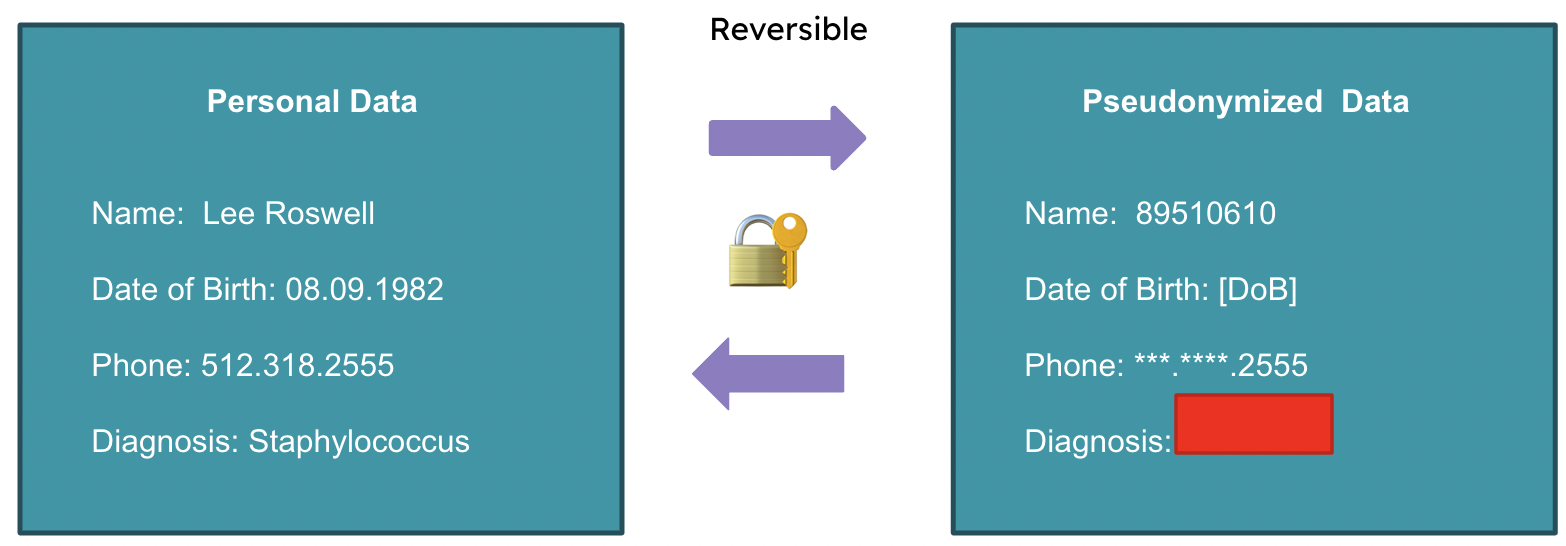
Pseudonymization
- False name
- Data is made unrecognizable, but can be returned to its original state
- Batman and Bruce Wayne

Pseudonymization example
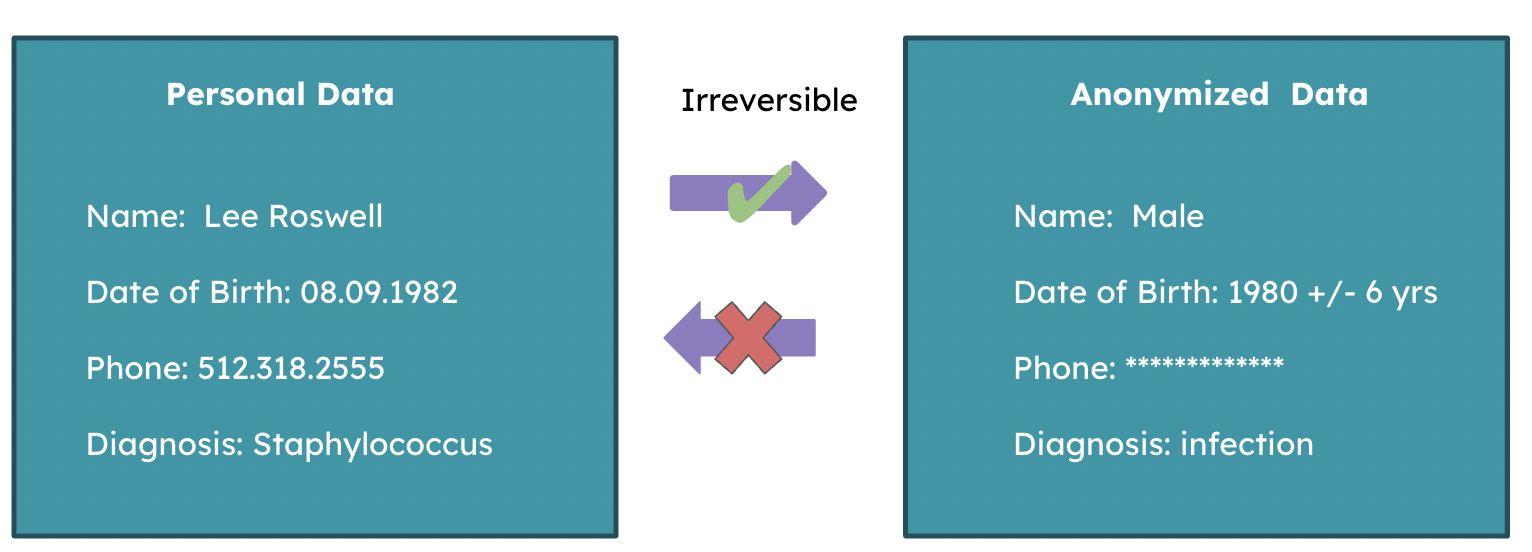
Anonymization
- Irreversible state change
- Removal of personal identifiers
- A human transforming into a zombie

Anonymization example
Let's practice!
Introduction to Data Privacy

