Security
Introduction to Data Privacy

Tiffany Lewis
Security and Privacy Instructor
Why are we talking about Security?
- Security is a precursor to Privacy.
- Security and Privacy programs are like an ice cream sundae:
- Security = ice cream
- Privacy = toppings

What is Information Security?
Information Security (InfoSec) - "The protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction in order to provide confidentiality, integrity, and availability."

1 https://www.nist.gov/blogs/cybersecurity-insights/next-generation-security-and-privacy-controls-protecting-nations
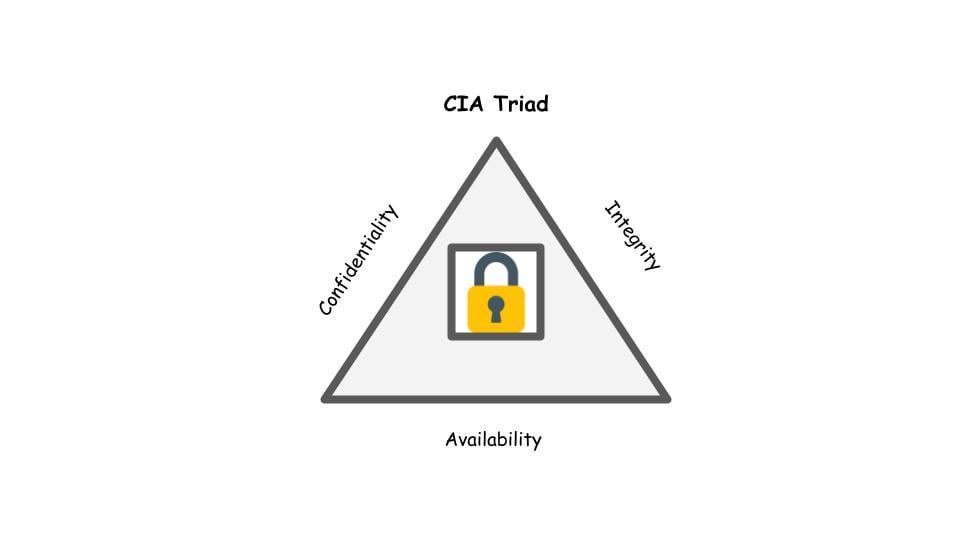
CIA Triad
- Popular security model
- CIA Triad helps companies identify and understand security controls
- Note: Many security models exist
- Example - DIE
- Distributed
- Immutable
- Ephemeral
- Example - DIE

CIA Triad breakdown
- CIA Triad represents:
- Confidentiality - data is protected and not accessed by unauthorized parties.
- Integrity - data is not altered or modified unexpectedly.
- Availability - data systems are running as expected.
Confidentiality - Identity Access Management (IAM)
- Confidentiality system's ability to ensure that only correct users have access to information.
- Identity Access Management (IAM)
- Ensures right people have access to the right resources at the right time.
- Real World Example - Limiting employee access to resources:
- Company email address
- Access to corporate network
- Access during working hours - 8AM to 5PM

Integrity - encryption and hashing
- Integrity - data can be trusted and has not been inappropriately modified
- Encryption - is a process that makes readable data undecipherable.
- "midnight" -> "Y!Iay.ig"
- Hashing- converting data to a standardized algorithmic output
- Encryption - is a process that makes readable data undecipherable.
- Real World: HTTPS communications
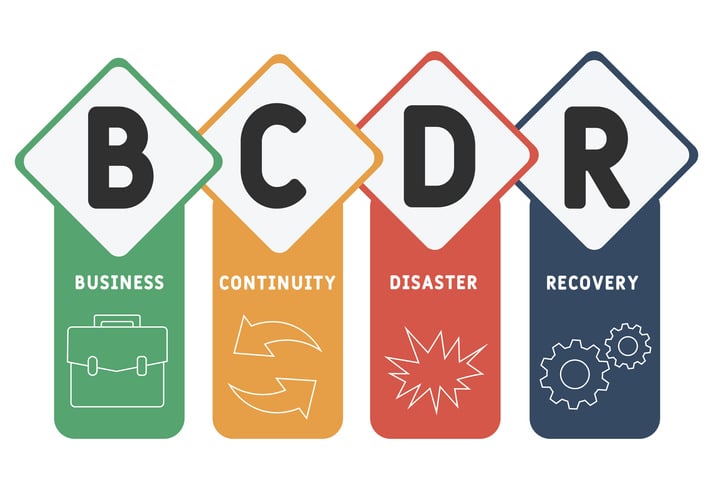
Availability - Business Continuity and Disaster Recovery
- Availability systems are accessible and available.
- Business Continuity and Disaster Recovery (BCDR) the processes, policies, and people used to help an organization continue during an unplanned event.
- Example - Flood damages data center
Let's practice!
Introduction to Data Privacy

