Création d'images Docker sécurisées
Présentation de Docker

Tim Sangster
Software Engineer @ DataCamp
Sécurité inhérente
Création d'images sécurisées
$$
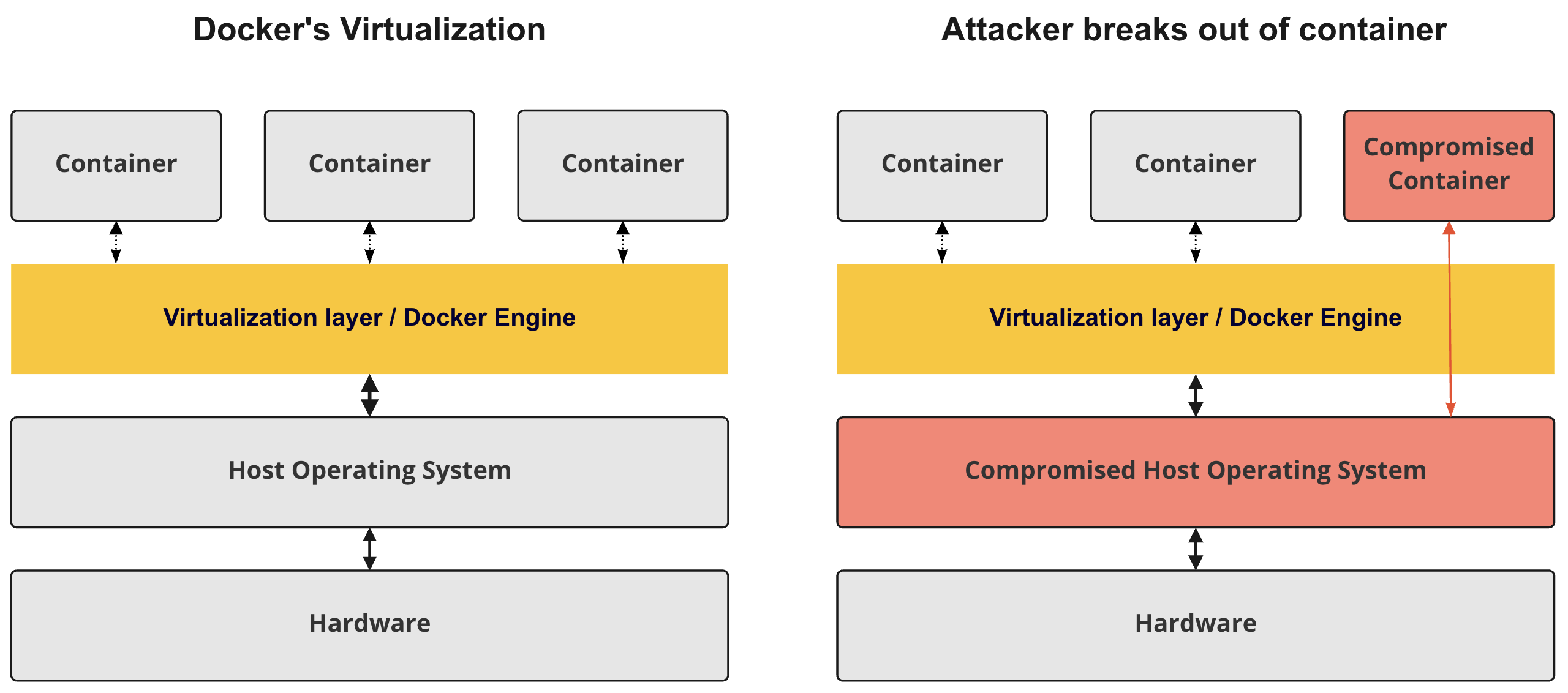
Les attaquants peuvent exceptionnellement s'échapper d'un conteneur.
$$
Des mesures de sécurité supplémentaires peuvent réduire ce risque.
$$
Cela devient particulièrement important lorsque des conteneurs en cours d'exécution sont exposés à Internet.
Images provenant d'une source fiable
Création d'images sécurisées -> Commencez par une image provenant d'une source fiable
Filtres Docker Hub :
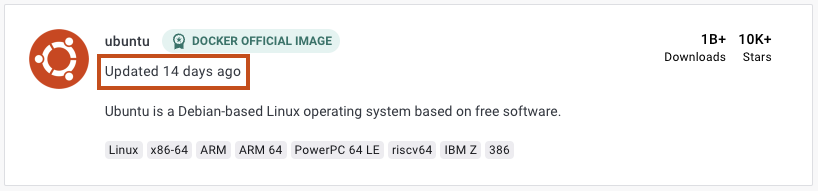
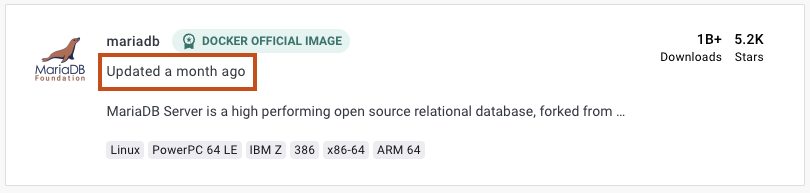
Gardez vos logiciels à jour
Limitez le nombre d'images
L'ajout de paquets non nécessaires peut compromettre la sécurité.
Ubuntu avec :
- Python2.7
- Python3.11
- Java JRE par défaut
- Java openjdk-11
- Java openjdk-8
- Airflow
- Notre application de pipeline
L'installation des paquets essentiels uniquement renforce la sécurité.
Ubuntu avec :
- Python3.11
- Notre application de pipeline
N’exécutez pas d'applications en tant qu'administrateur root
Autoriser l'accès root à une image empêche de la maintenir à jour et d’en limiter le nombre.
Au lieu de cela, démarrez les conteneurs en tant qu'utilisateur disposant de moins d’autorisations :
FROM ubuntu # User is set to root by default.
RUN apt-get update
RUN apt-get install python3
USER repl # We switch the user after installing what we need for our use-case.
CMD python3 pipeline.py
Passons à la pratique !
Présentation de Docker

