Advanced Key vault settings
Implement Azure Security for Developers

Anushika Agarwal
Cloud Data Engineer
Entra ID powers Key vault authentication
- First step of accessing Key Vault = Authentication
- Key Vault uses Microsoft Entra ID for authentication

Identity types in Key vault
- User: A person

- Group: A set of users

- Service Principal: An app or service identity

App authentication methods
- Managed Identity (recommended)
- No secrets, managed by Azure

- App Registration
- Manual setup, credentials required

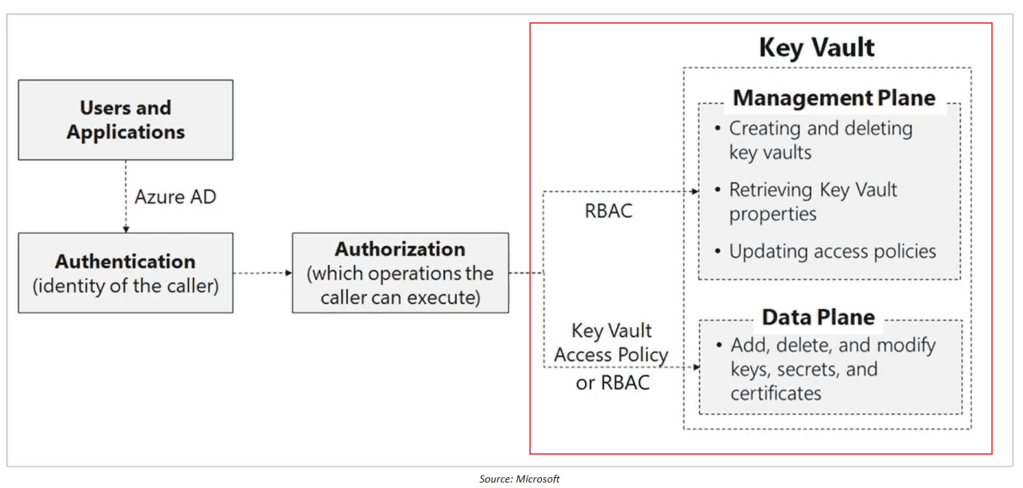
Authorization in Key vault
After authentication, authorization defines what you can do
Azure offers two authorization models - Access Policies and RBAC
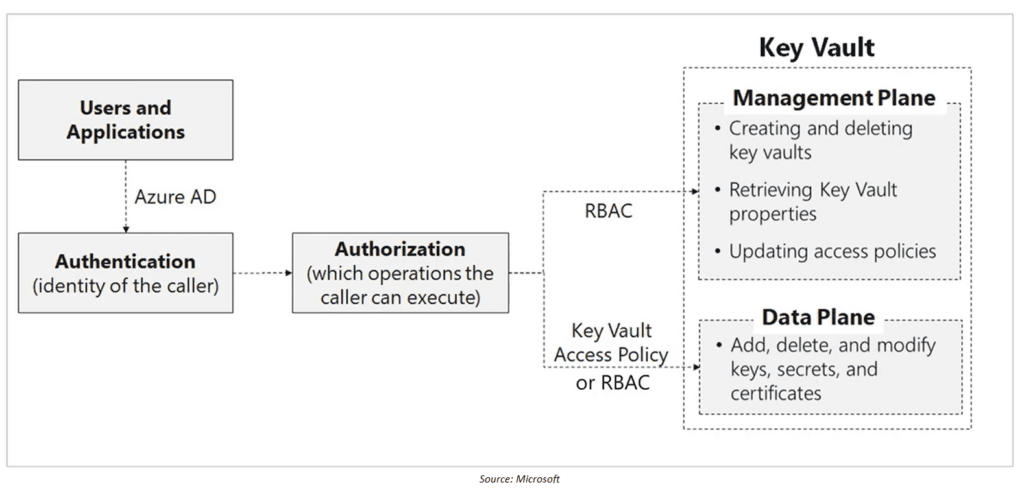
Access policies (legacy)
- Control data plane only (inside Key Vault)
- No control over the management plane or who can manage the vault
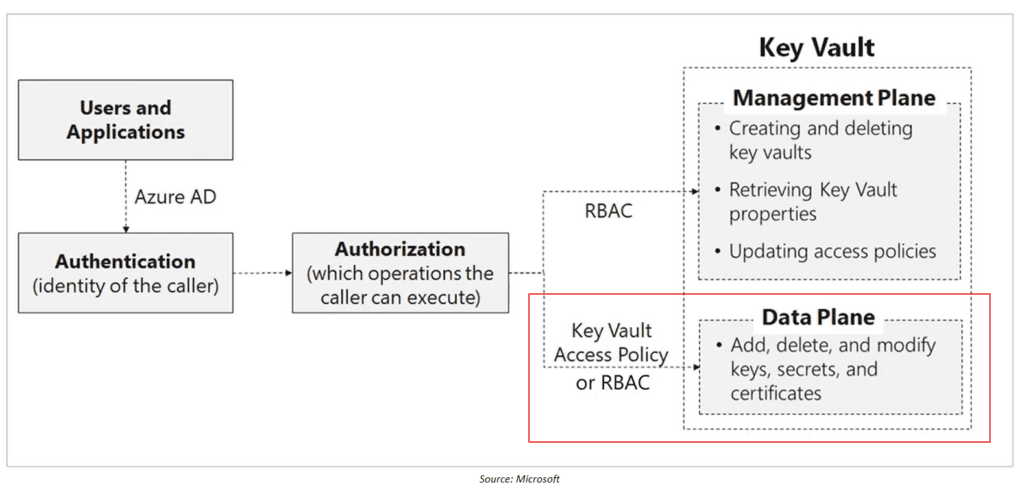
RBAC: Role-Based Access Control (recommended)
- Controls access to
- Management Plane: Vault itself
- Data Plane: Keys, Secrets, Certificates
- Supports PIM, MFA, Conditional Access
Soft delete
Status quo:
- Deleted items can cause a major disruption
Soft Delete Enabled:
- Deleted items enter a recoverable state
- Protects against accidental or malicious deletion

Where soft delete applies?
- Vault

Keys

- Secrets

- Certificates

Soft delete configuration
- Retain duration - 7-90 days (default: 90)
- Enabled by default for new vaults
- Cannot be turned off once configured
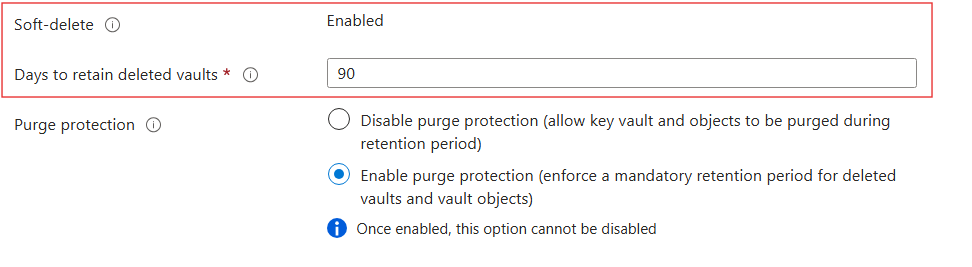
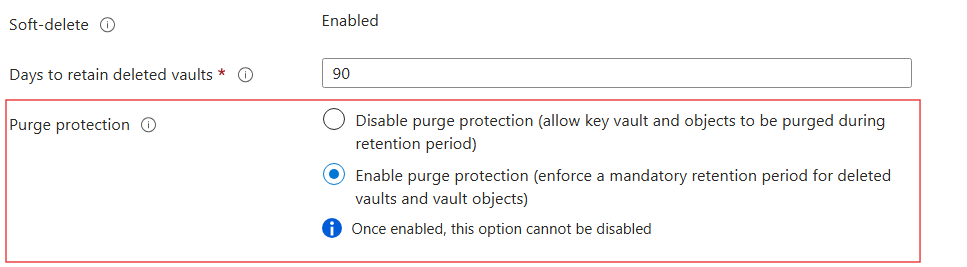
Purge protection
- Purge = permanent deletion with no recovery
- Blocks purging during retention
- Even admins can't purge

Where purge protection applies?
- Vault

Keys

Secrets

- Certificates

Purge protection configuration
- Configuration
- Retain duration - 7-90 days (default: 90)
- Requires Soft Delete to be enabled
- Cannot be turned off once configured
Best practices
Design for Isolation
- Use separate vaults
Control Access
- Access only for trusted users and apps

- Enable Resilience
- Turn on backups after updates or deletions
- Enable Soft Delete and Purge Protection
Monitor Activity
- Enable diagnostic logging and alerts

Let's practice!
Implement Azure Security for Developers

