Shared Access Signatures (SAS)
Implement Azure Security for Developers

Anushika Agarwal
Cloud Data Engineer
What is a shared access signature?
- Grants limited access to storage resources
- Does not expose the storage account key
Analogy: SAS as a vending token
Token valid for limited time (e.g., 30 seconds)
Token allows specific action only (e.g., one Coca-Cola)

How a SAS is secured?
- Signed with storage account key

- Or with Microsoft Entra ID

Types of SAS
- User delegation SAS
- Uses Microsoft Entra credentials
- Works with Blob and Data Lake Storage
- Service SAS
- Uses storage account key
- Access to one service: Blob, Queue, Table, or File
- Account SAS
- Uses storage account key
- Access to multiple services
- Service level operations
Real-world scenario
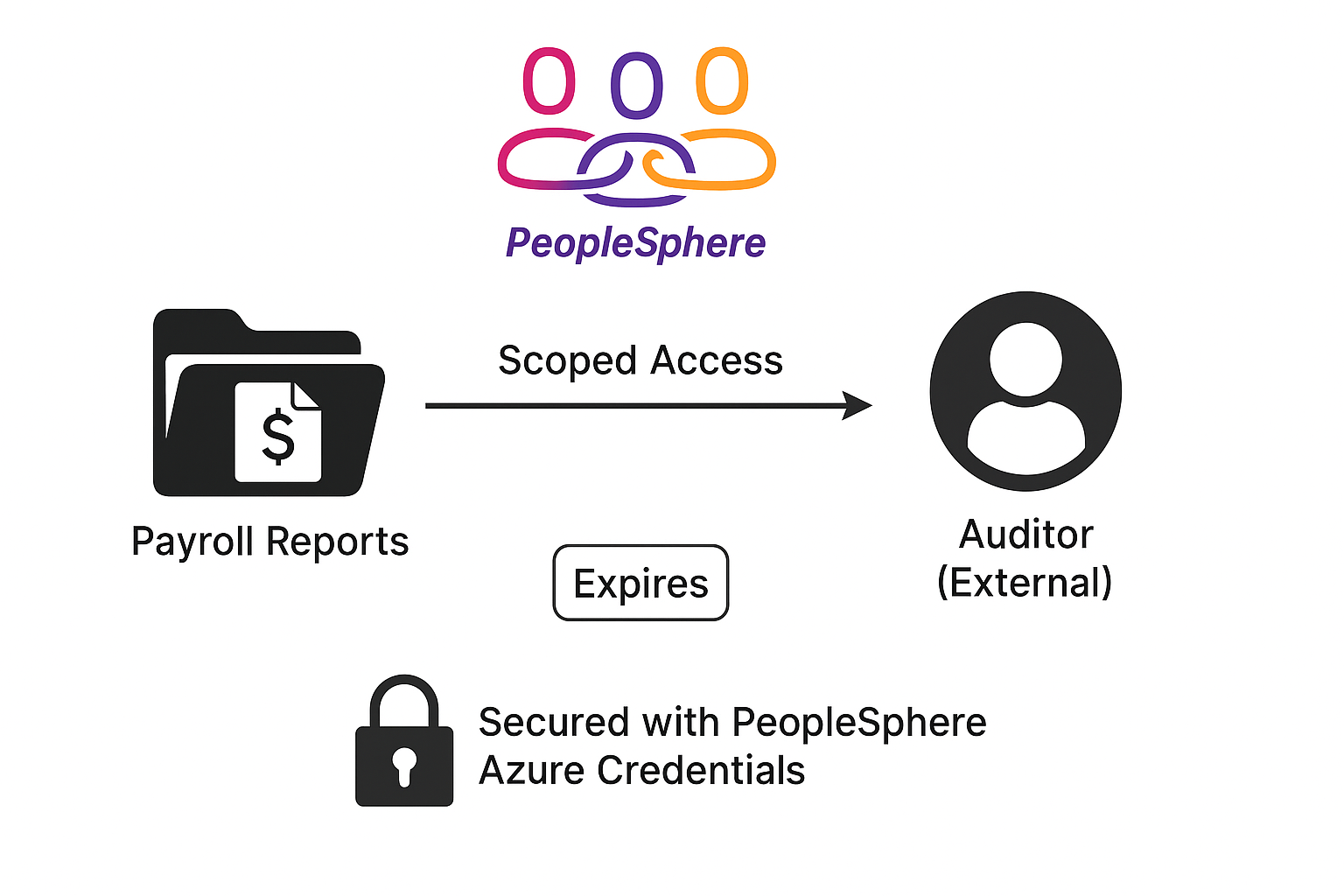
Scenario:
- PeopleSphere shares payroll reports with an external auditor
SAS Type: User Delegation SAS
Scoped access:
- Auditor sees only the required reports
Time-bound:
- Access expires automatically
Securely authenticated:
- PeopleSphere's Azure credentials
Understanding SAS structure
Components of a SAS
- URI - Resource Path
- Token - Access Rules & Signature

Token components

sp: Permissions (e.g., r = read, w = write)st/se: Start and expiry timespr: Protocol (e.g., https only)sr: Resource type (b = blob, f = file)sv: Storage API versionsig: Signature used for validation
Best practices for using SAS
- Always use HTTPS
- Prefer User Delegation SAS
- Set short expiry times
- Grant minimal permissions

- Avoid SAS for high-risk access

Let's practice!
Implement Azure Security for Developers