Microsoft identity platform
Implement Azure Security for Developers

Anushika Agarwal
Cloud Data Engineer
What is the Microsoft identity platform?
- Manages app sign-ins and access
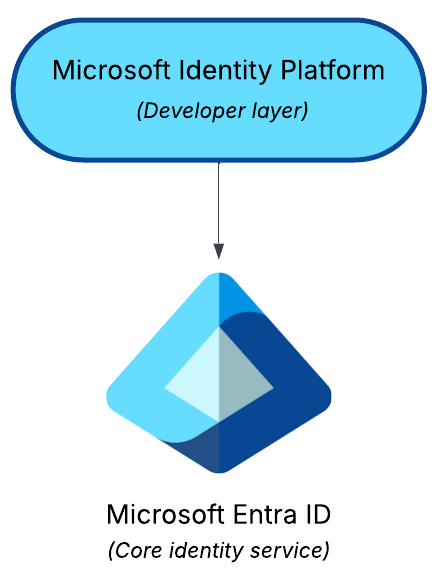
- Built on Microsoft Entra ID
- Entra ID = Core Identity Service
- Identity Platform = Developer Layer for Apps
- Built on Microsoft Entra ID
How it works?
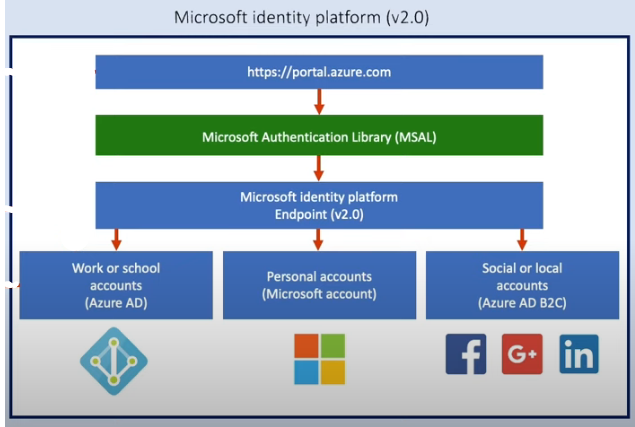
- Authenticates:
- Standards:
- OAuth 2.0: limits what apps can do
- OpenID Connect: confirms who you are
- OAuth 2.0: limits what apps can do
- Account Types
- Enterprise/school accounts
- Personal Microsoft accounts
- Social/local accounts
- Standards:
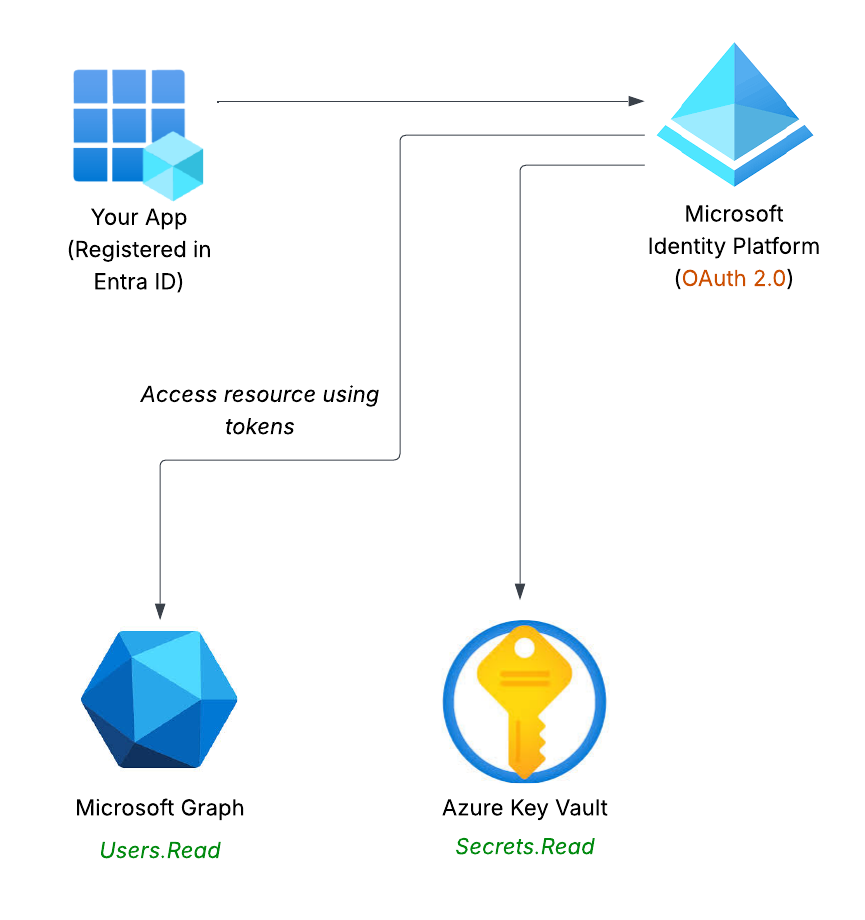
Key tools of the Microsoft identity platform
- MSAL:
- request tokens for apps
![]()
- App registration:
- set up app identity in Azure

- Microsoft Graph API:
- access users, groups, and resources

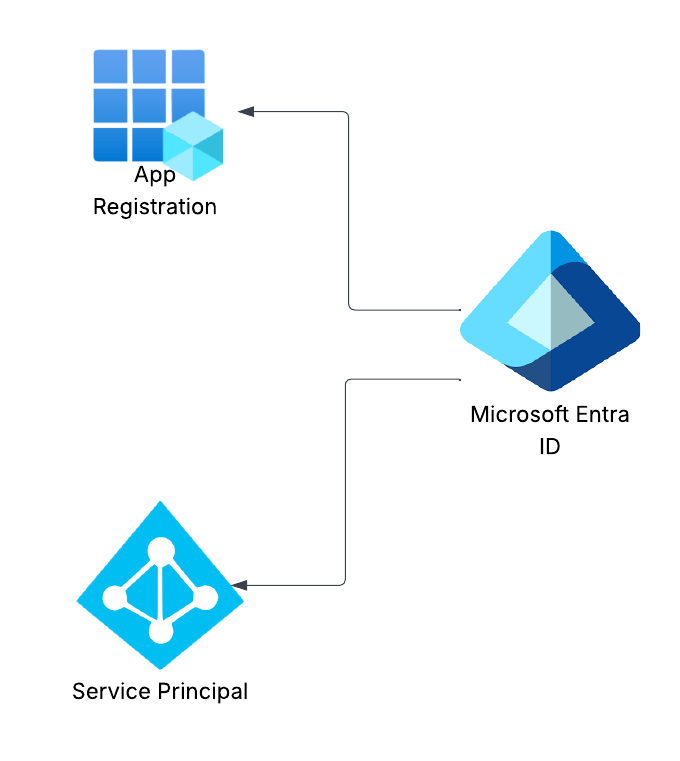
App registration
Registering apps connects them to Entra ID
Choose:
- Single-tenant: app works only in your org
- Multi-tenant: app works across orgs
Automatically creates:
- Application object
- Service principal
Add secrets, certificates, scopes, and branding
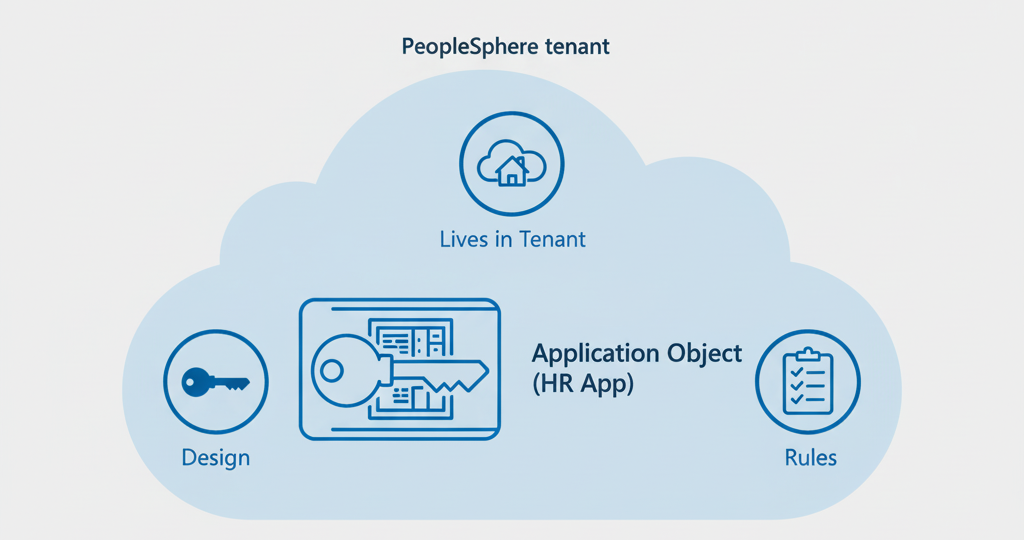
Application object
- Blueprint of the app
- Lives in your home tenant
- Defines authentication and access rules

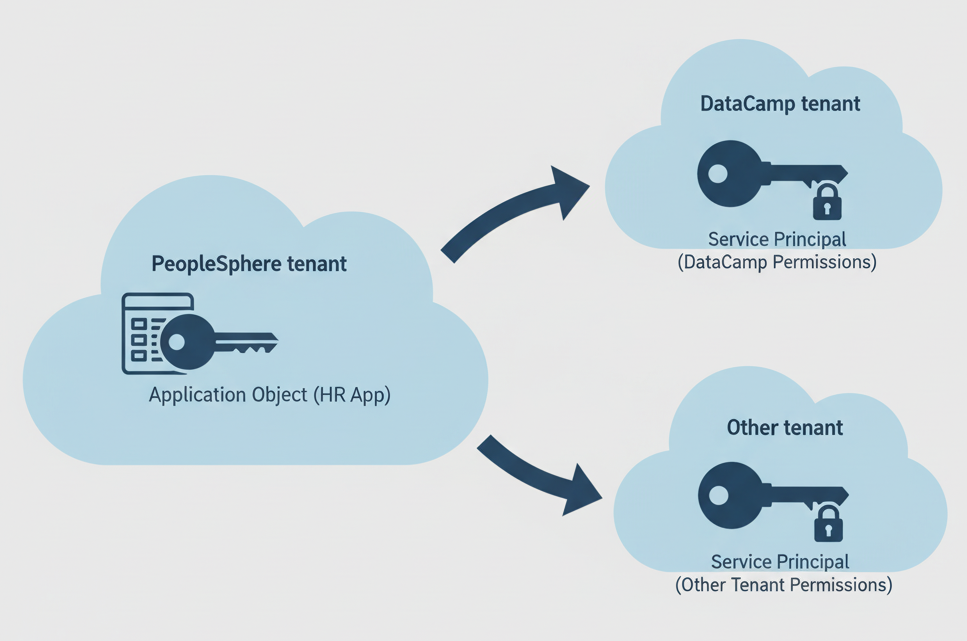
Example: application object in PeopleSphere
- PeopleSphere creates an HR app in its own tenant
Service principal
- Instance of the app in each tenant
- Working copy of the original key
- Each customer gets their own service principal in their tenant

Example: service principal in DataCamp
- Service Principal created in DataCamp's tenant
Types of service principal
- Application:
- Standard app instance

- Managed Identity:
- secret-free access

- Legacy:
- Older apps

Permissions
Apps request access using OAuth 2.0 and permission scopes
graph.microsoft.com/Calendars.Read

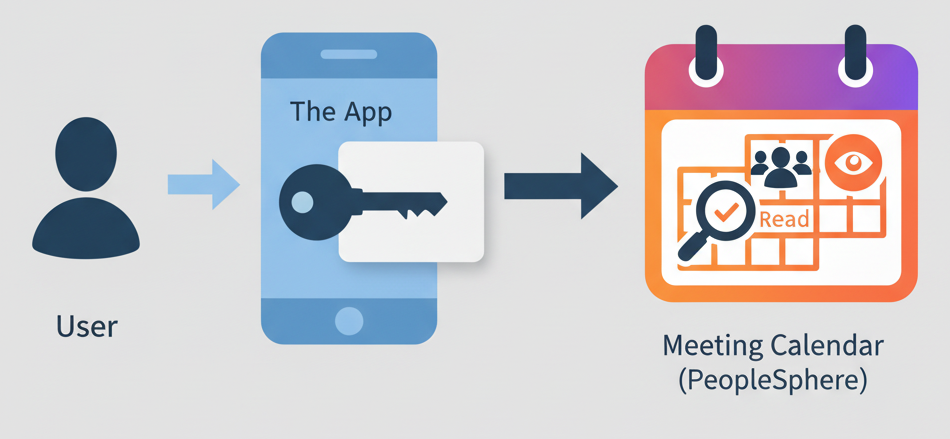
Delegated permissions
App acts on behalf of the user
Requires a signed-in user
Example: PeopleSphere schedules meetings for DataCamp users
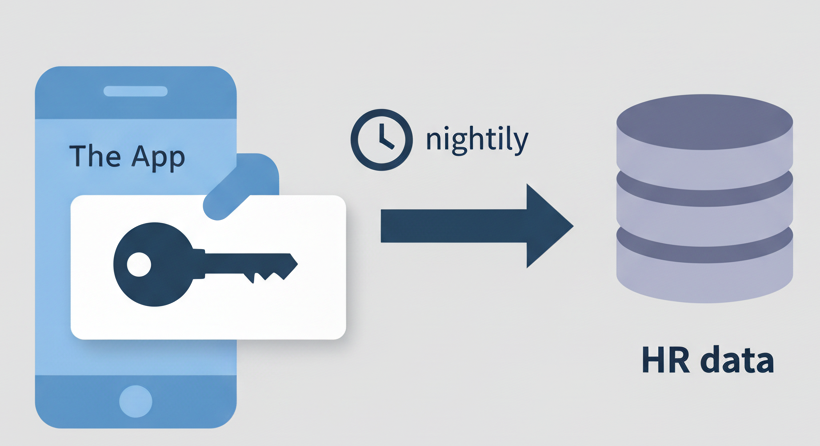
App-only permissions
- App acts as itself
- No user involvement
- Example: PeopleSphere syncs HR data nightly
Consent
Apps need consent to activate permission scopes
Consent Types:
- Static: permissions set during registration
- Incremental: added as needed
- Admin: required for high-privilege access

Let's practice!
Implement Azure Security for Developers

