Cloud security in Azure
Understanding Microsoft Azure Architecture and Services

Florin Angelescu
Azure Architect
Cloud security

- Protection of data, applications, and infrastructure
- Involves practices like:
- Data encryption
- Identity management
- Network security
- Compliance adherence
- Measures to detect and respond to security incidents
Cloud security

- Responsibility is shared between the cloud service provider and the users
- Aims to ensure the confidentiality, integrity, and availability of information
Zero trust model

- Assumption of a potential breach
- Safeguards resources accordingly
- Verifies each request as if it originated from an unsecured network
Zero trust - explicit verification
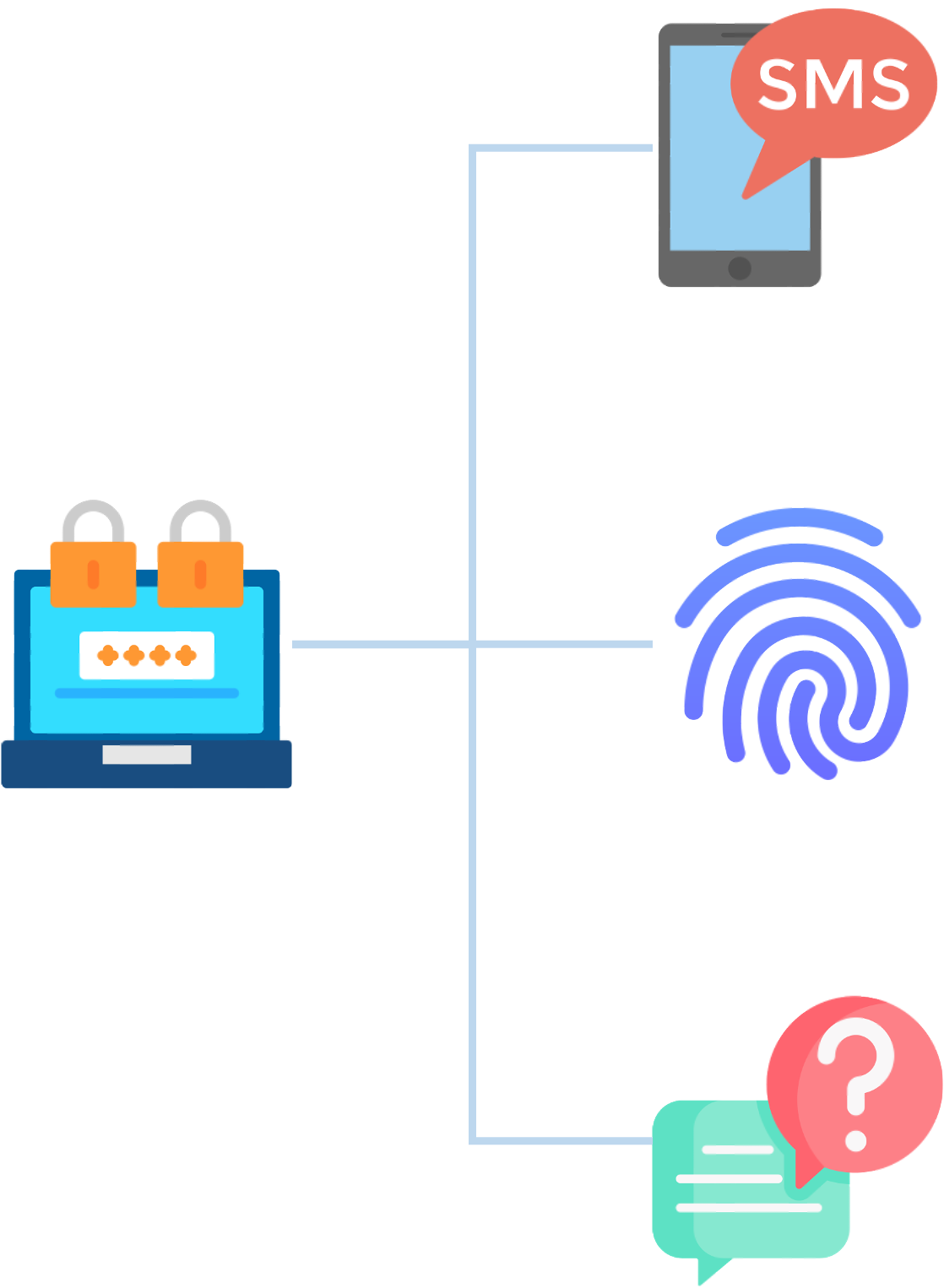
- Always authenticate and authorize based on all available channels
Zero trust - least privilege access
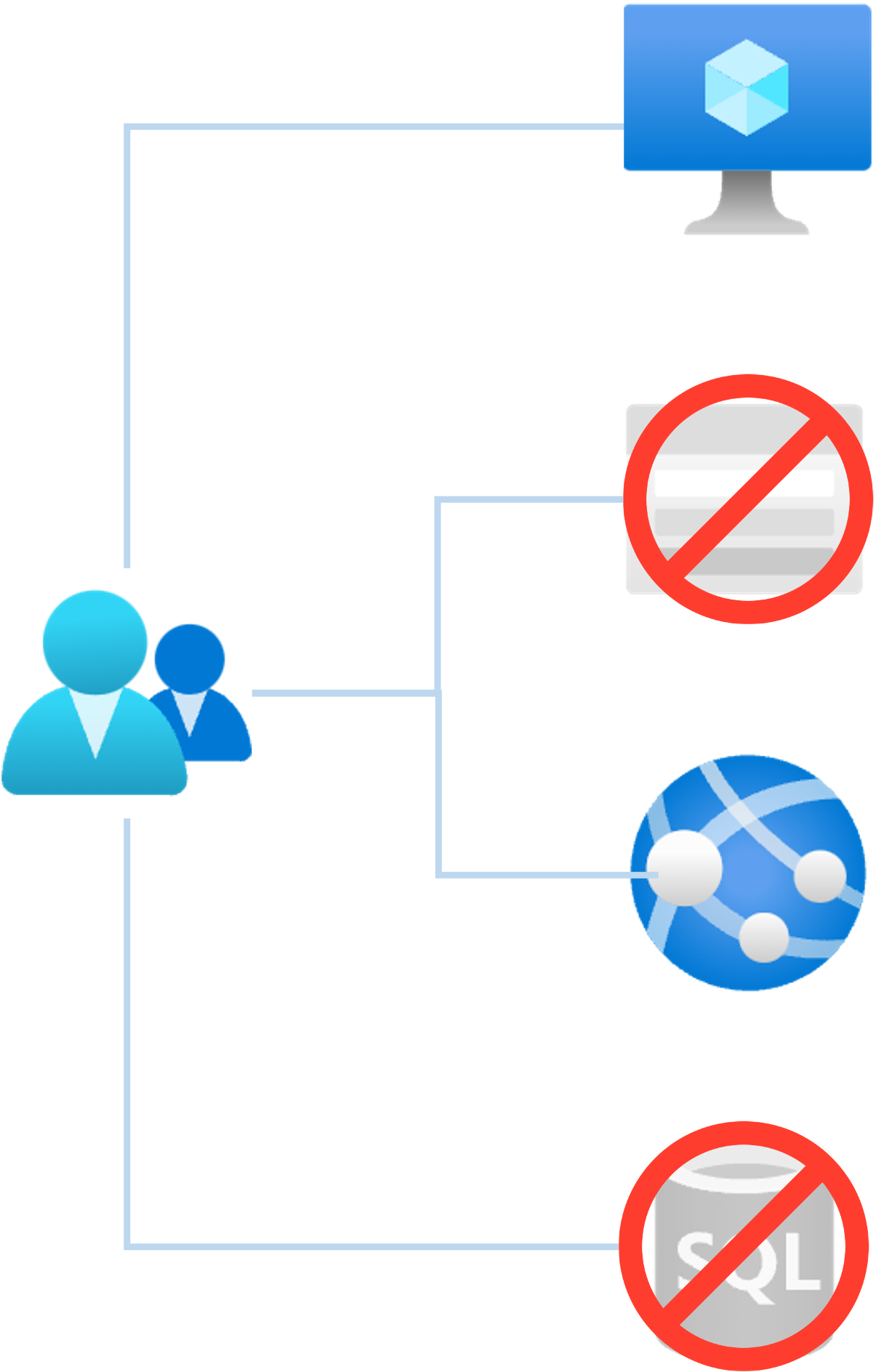
- Users should only be granted access to the resources and permissions essential for their specific job roles
Zero trust - assume breach
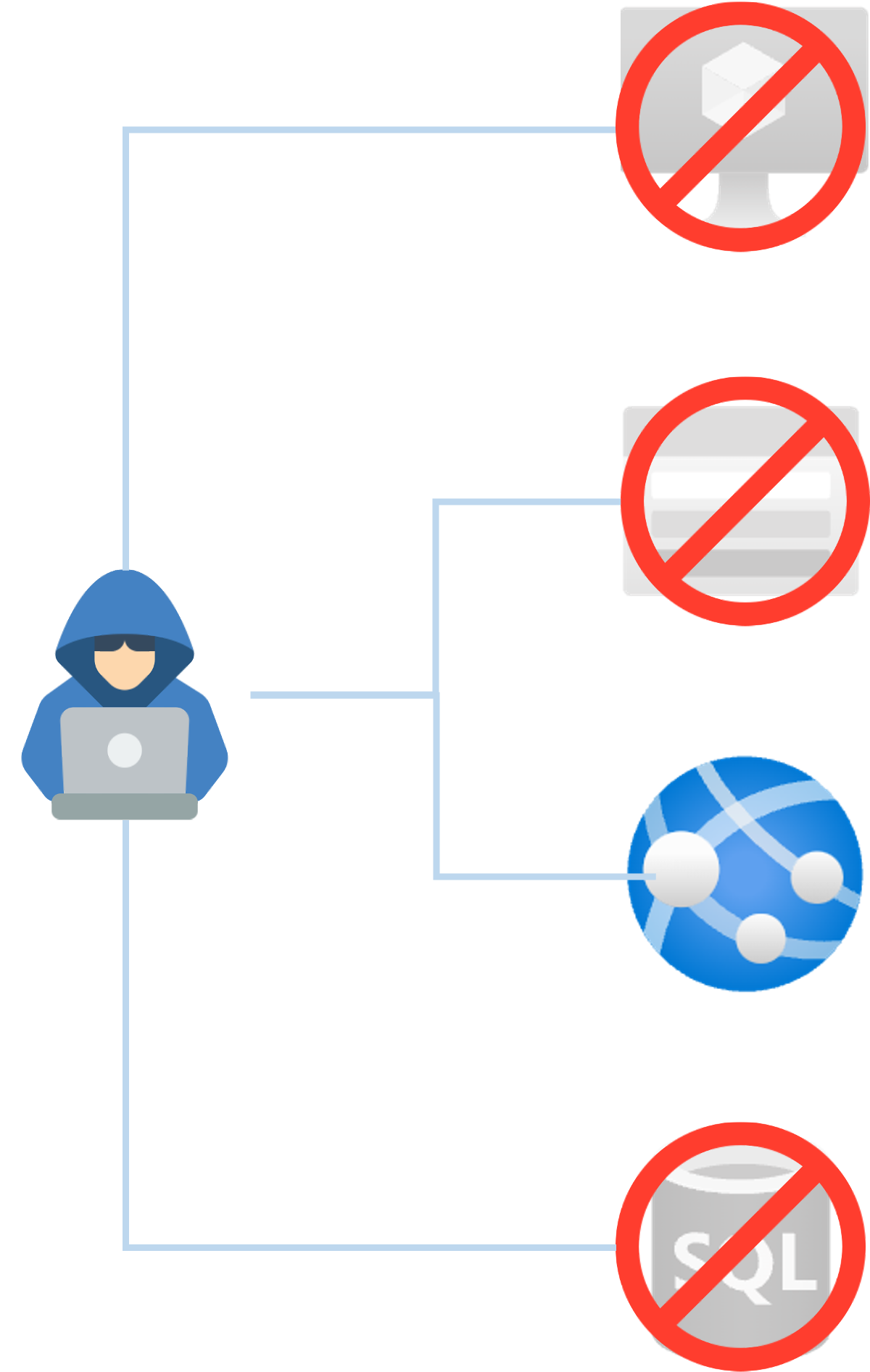
- Determined attackers may find a way in
- Minimize the impact of a breach
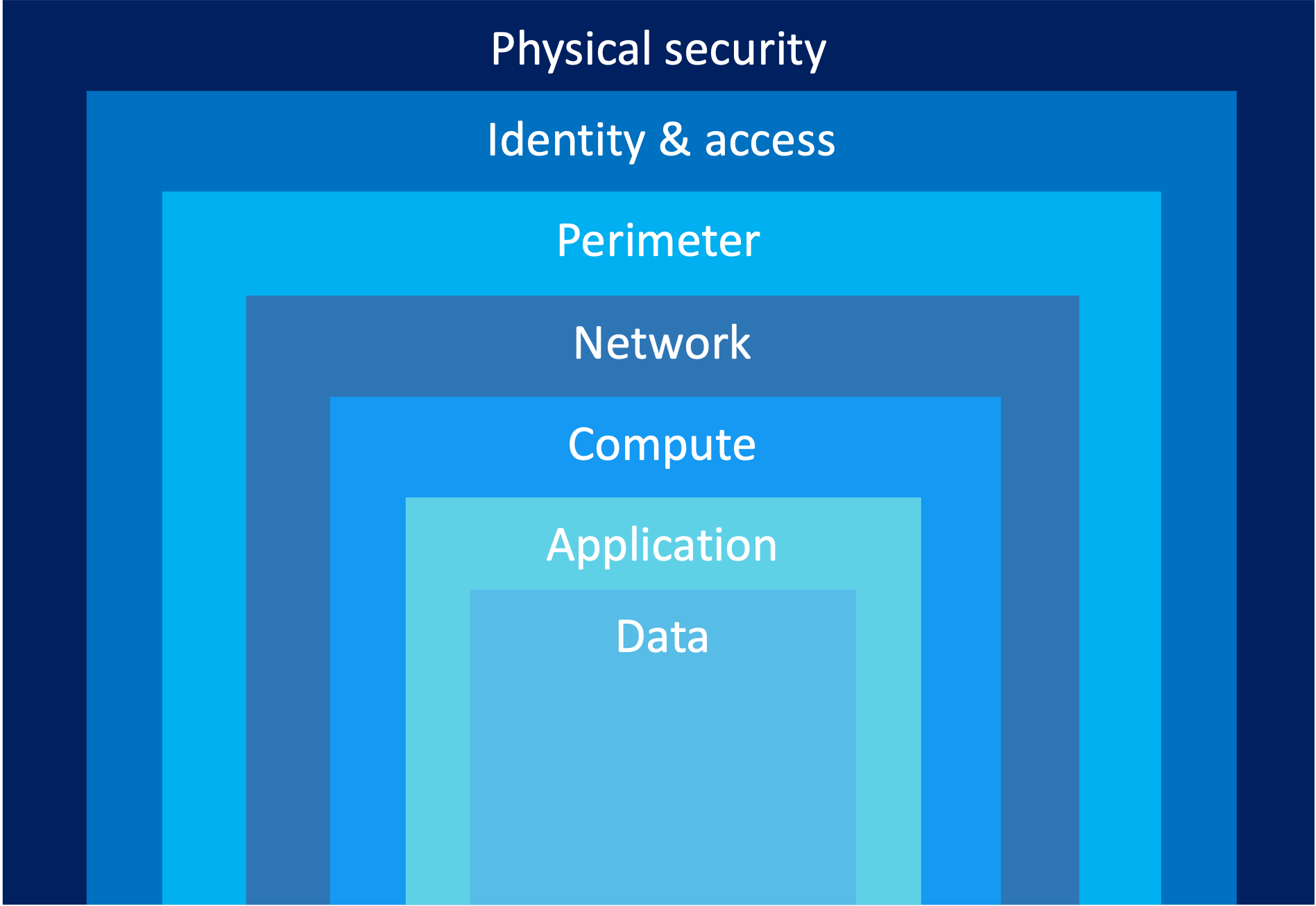
Defense-in-depth

- Safeguard resources and prevent unauthorized access and information theft
- Employs multiple layers of mechanisms to block the progress of an attack
- Central data is surrounded by protective layers to ensure its security
Defense-in-depth layers
Microsoft Defender for Cloud

- Monitoring tool for security posture management and threat protection
- Provides guidance and notifications to enhance security
- Integrates into Azure natively
Assess, secure and defend

Importance of cloud security

- Foundation of trust in our digital landscape
- Protects data, applications, and systems
- Ensures confidentiality, integrity, and availability
Let's practice!
Understanding Microsoft Azure Architecture and Services

