Securing Applications in AKS
Azure Compute Solutions

Florin Angelescu
Azure Cloud Architect
Why security matters
- Critical in any production environment.
- Containers and Kubernetes introduce new layers of complexity.
- Workloads can be exposed to risks.
Why security matters
AKS integrates with Azure's security ecosystem to protect:
- Applications
- Data
- Users
Strong security practices:
- Build trust with customers and stakeholders
- Proving that workloads are resilient and well-managed
Role-Based Access Control (RBAC)

- Control who can perform actions in the cluster.
Role-Based Access Control (RBAC)
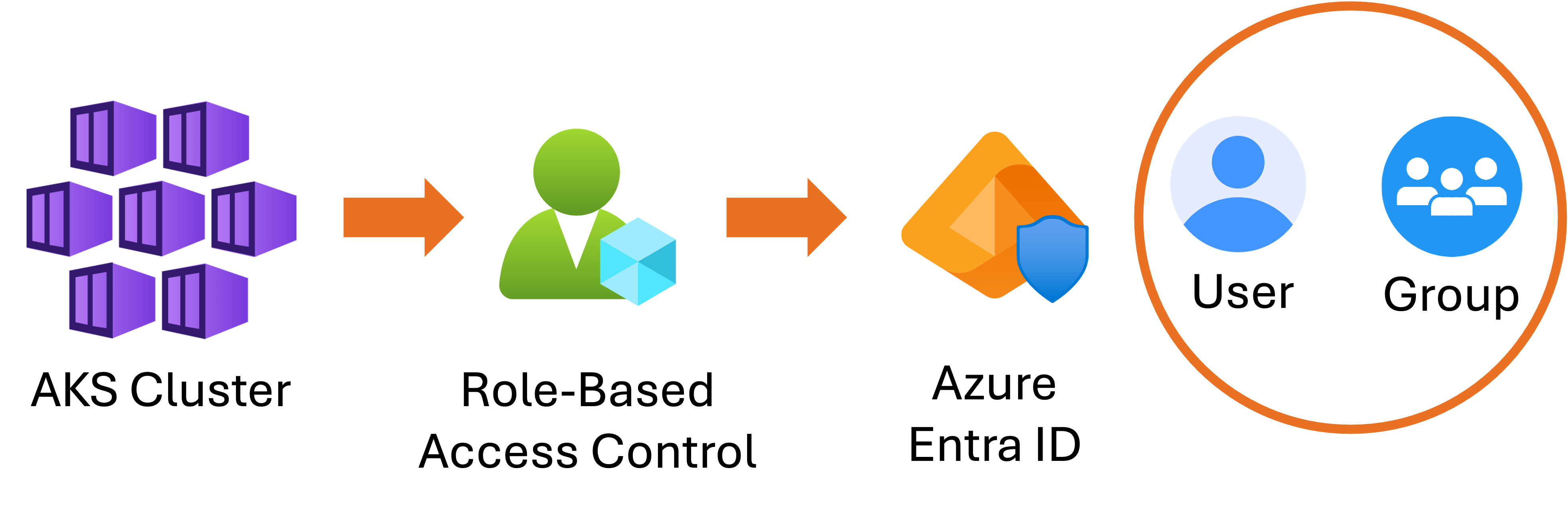
- Control who can perform actions in the cluster.
Integrates with Entra ID:
- Assign roles to users or groups
Only authorized individuals can deploy, scale, or modify workloads.
Role-Based Access Control (RBAC)
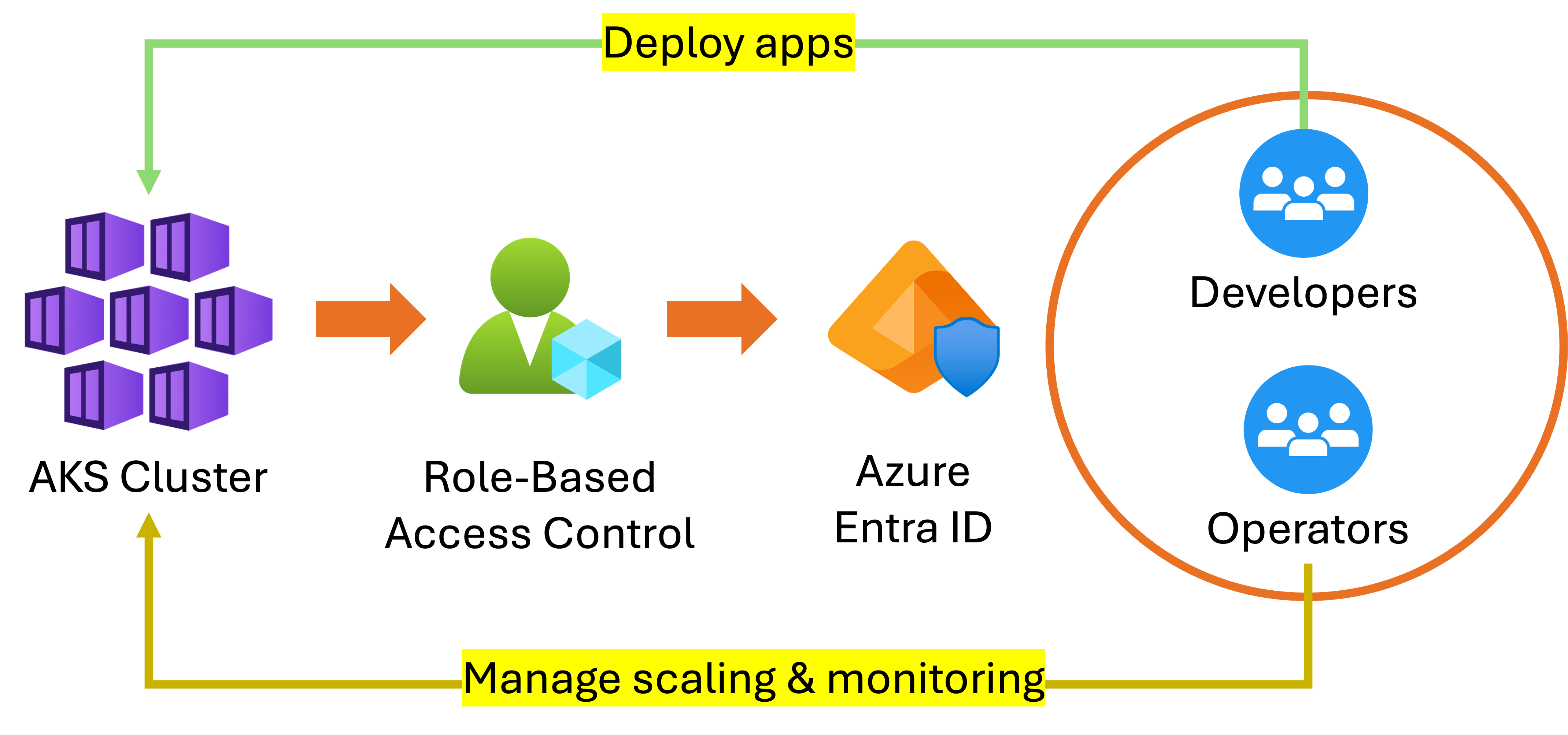
- Developers have permissions to deploy apps.
- Operators manage scaling and monitoring.
- Granular role assignments reduce the risk of accidental or malicious changes.
Secrets management
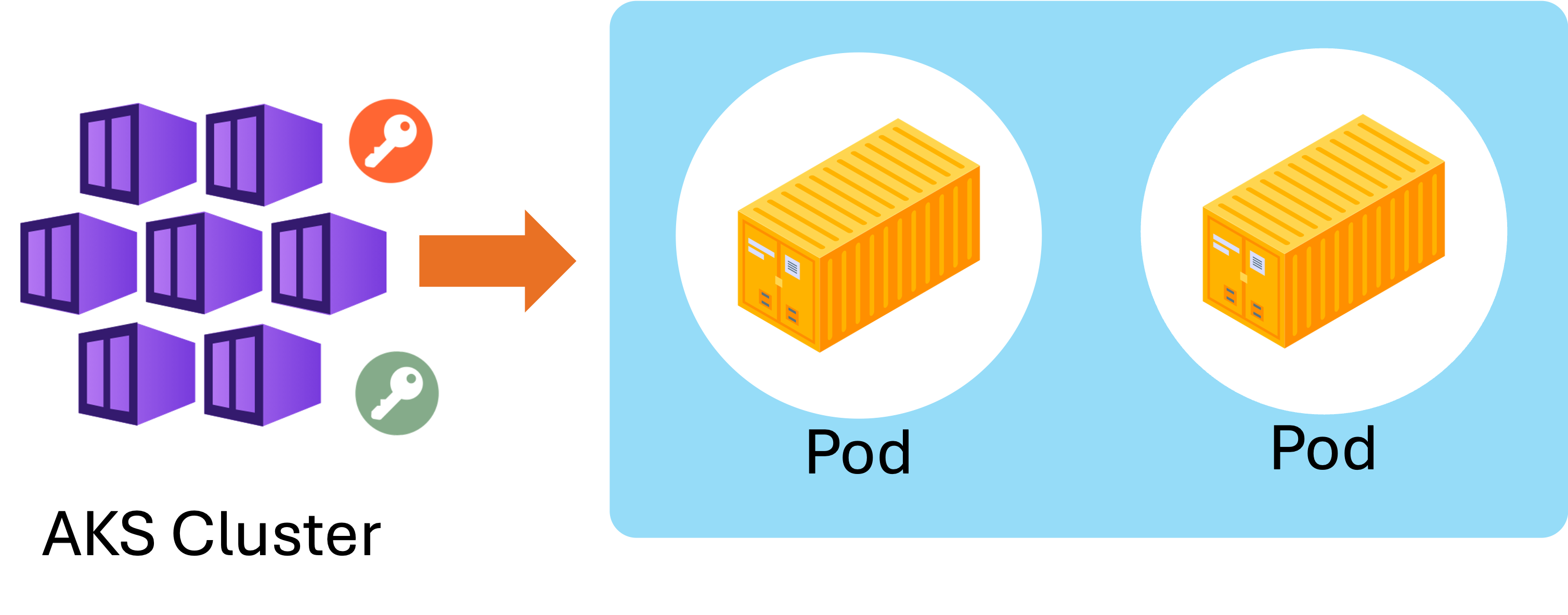
Applications require sensitive information:
- Passwords
- API keys
- Certificates
Kubernetes stores these as secrets.
- Can be mounted into pods securely.
Secrets management
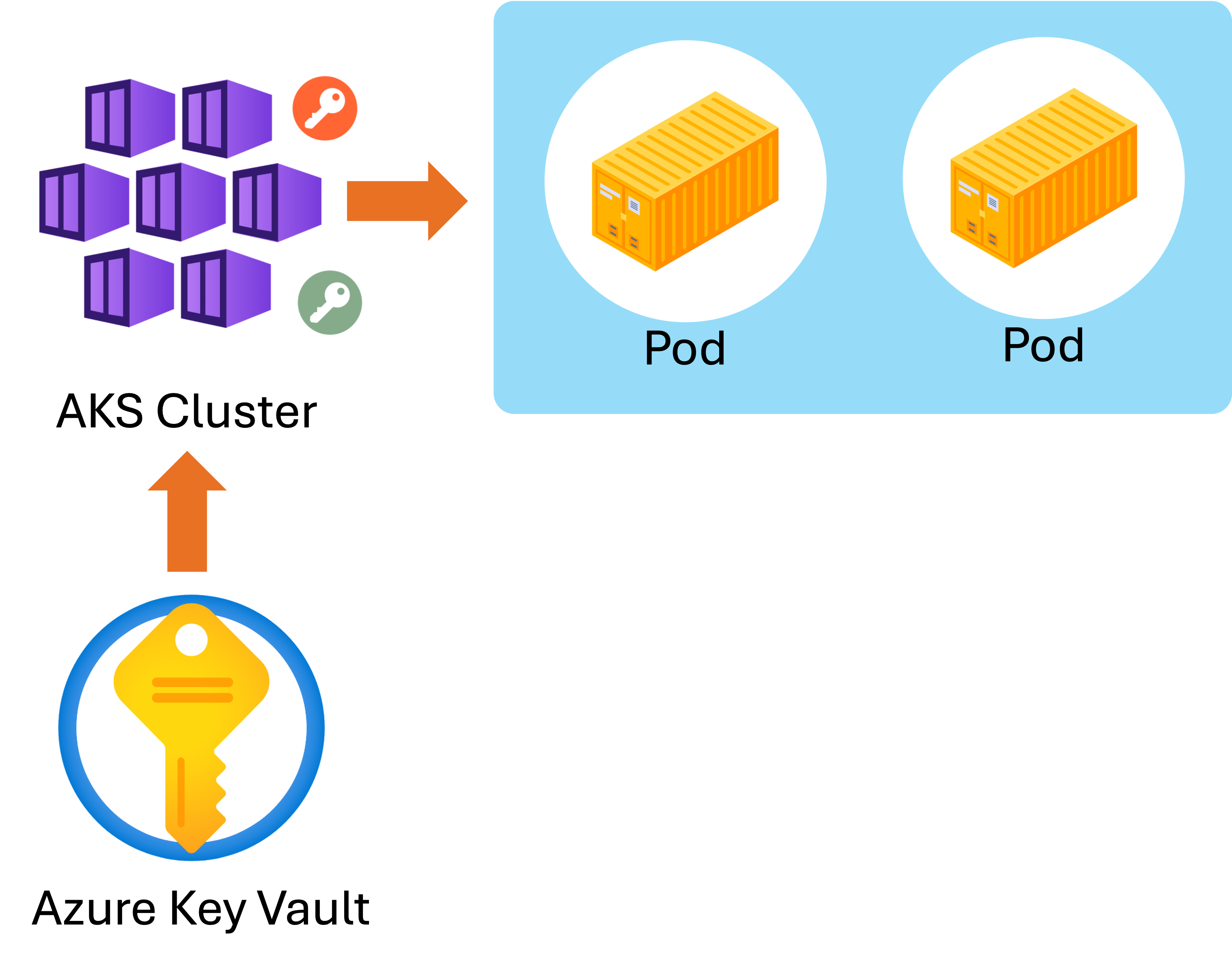
- Secrets can integrate with Azure Key Vault:
- Centralized management and encryption
- Sensitive data is never hard-coded into images or manifests.
- Reduces the risk of leaks.
- Rotate secrets regularly.
Network security
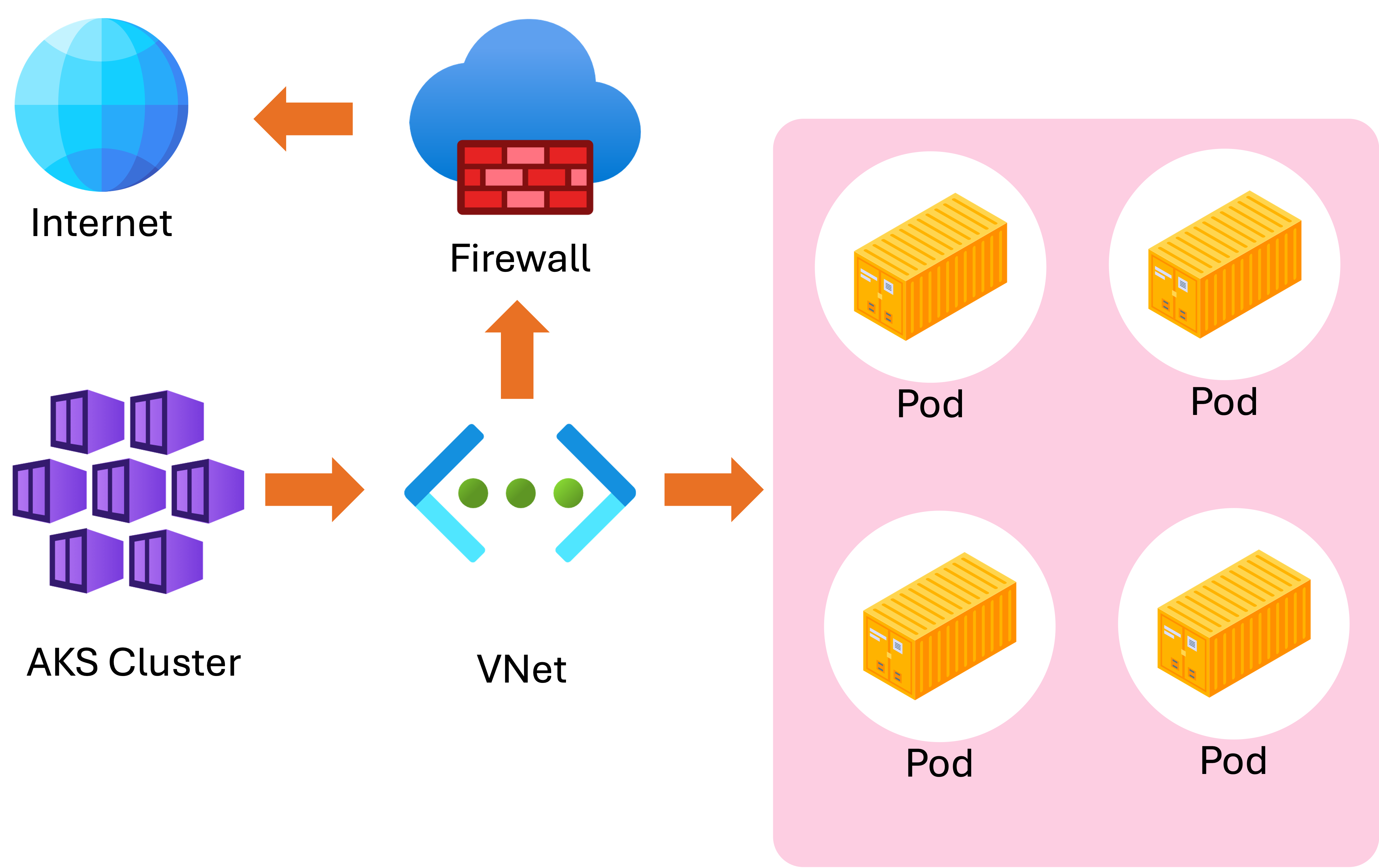
- AKS clusters run inside Azure Virtual Networks:
- Network security groups
- Firewalls
Network security
AKS clusters run inside Azure Virtual Networks:
- Network security groups
- Firewalls
Restrict traffic between pods.
- Enforce policies.
- Isolate workloads.
Network security
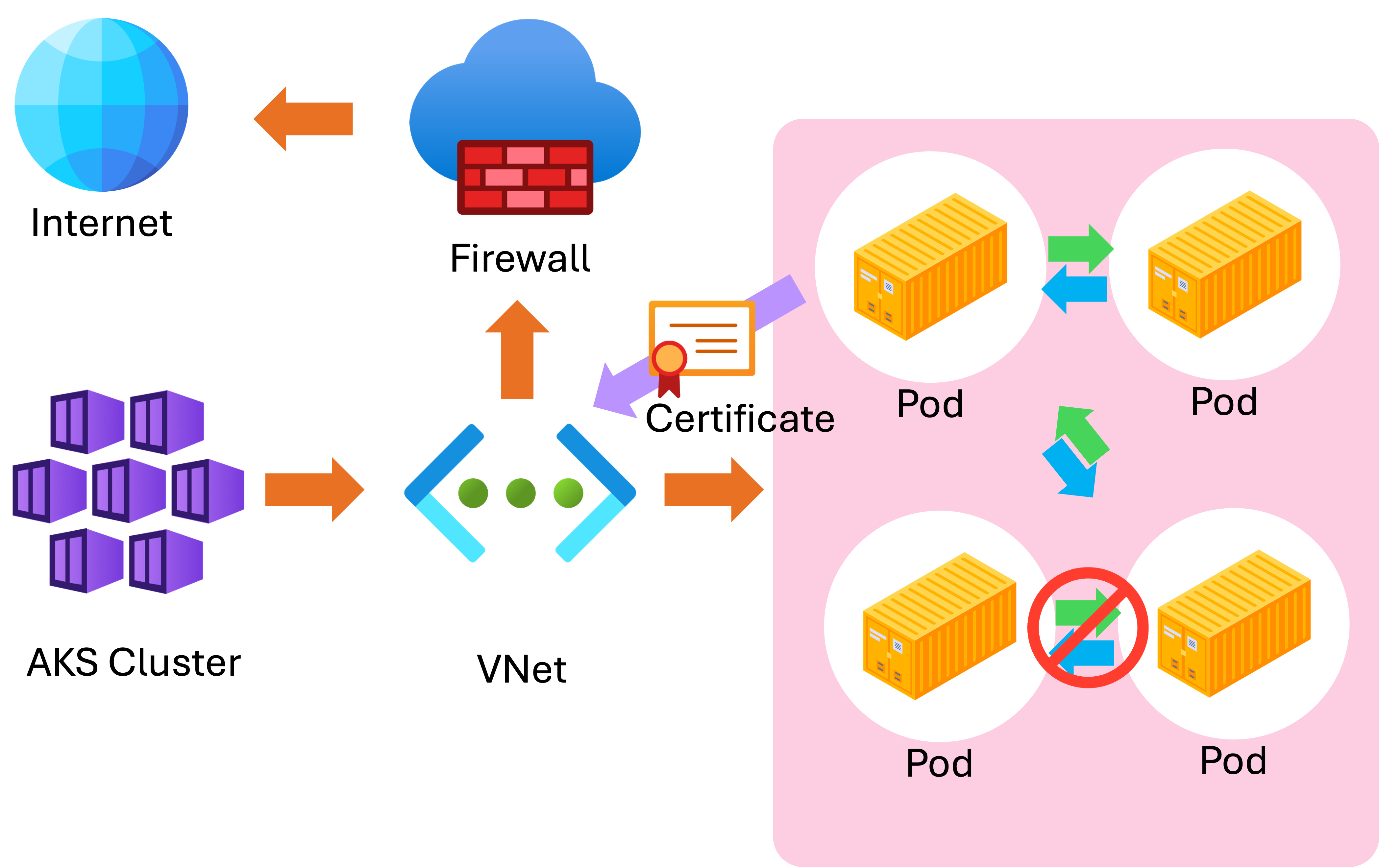
- Ingress controllers:
- Configured with TLS certificates
- Secure external traffic
Network security
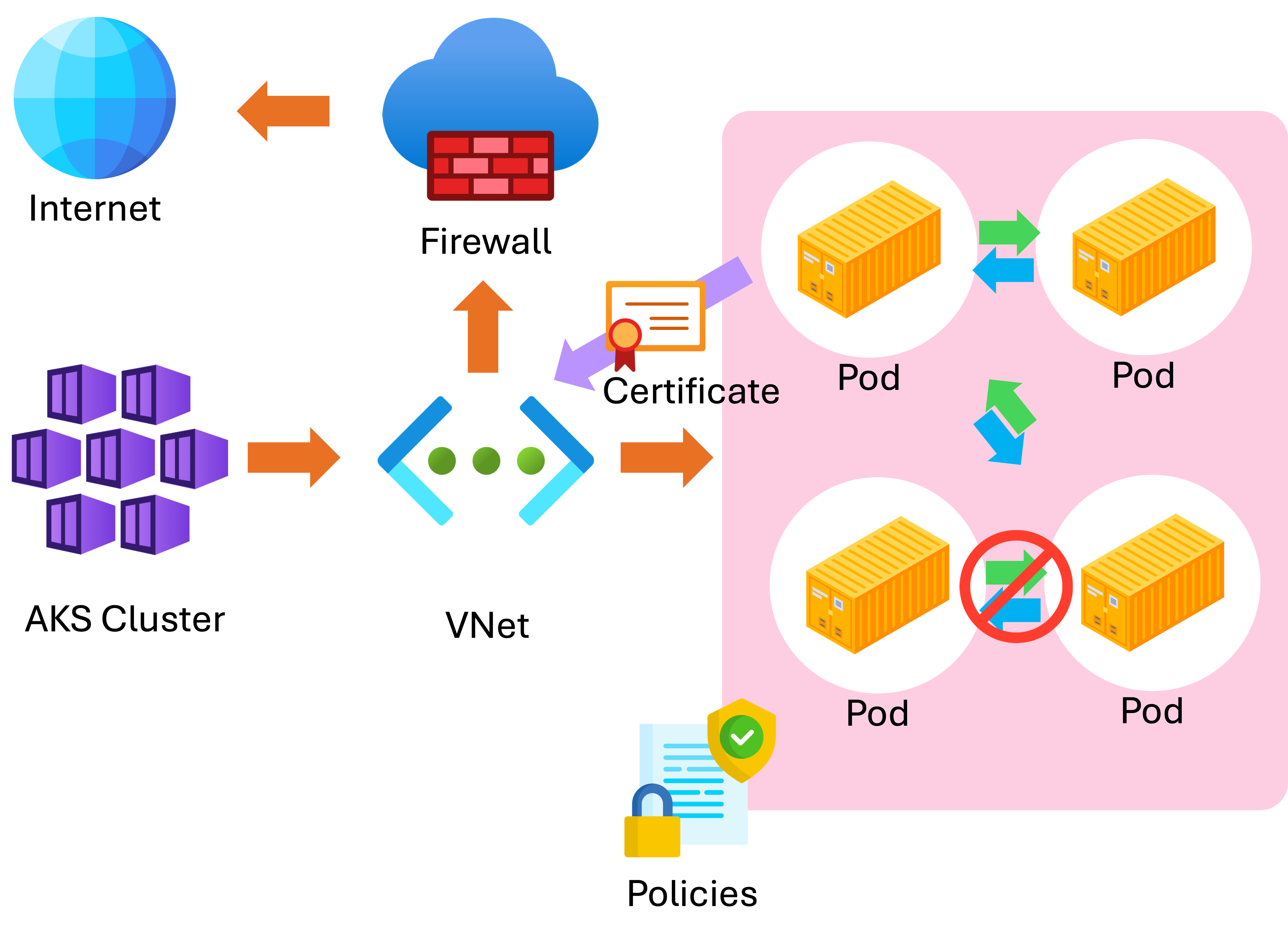
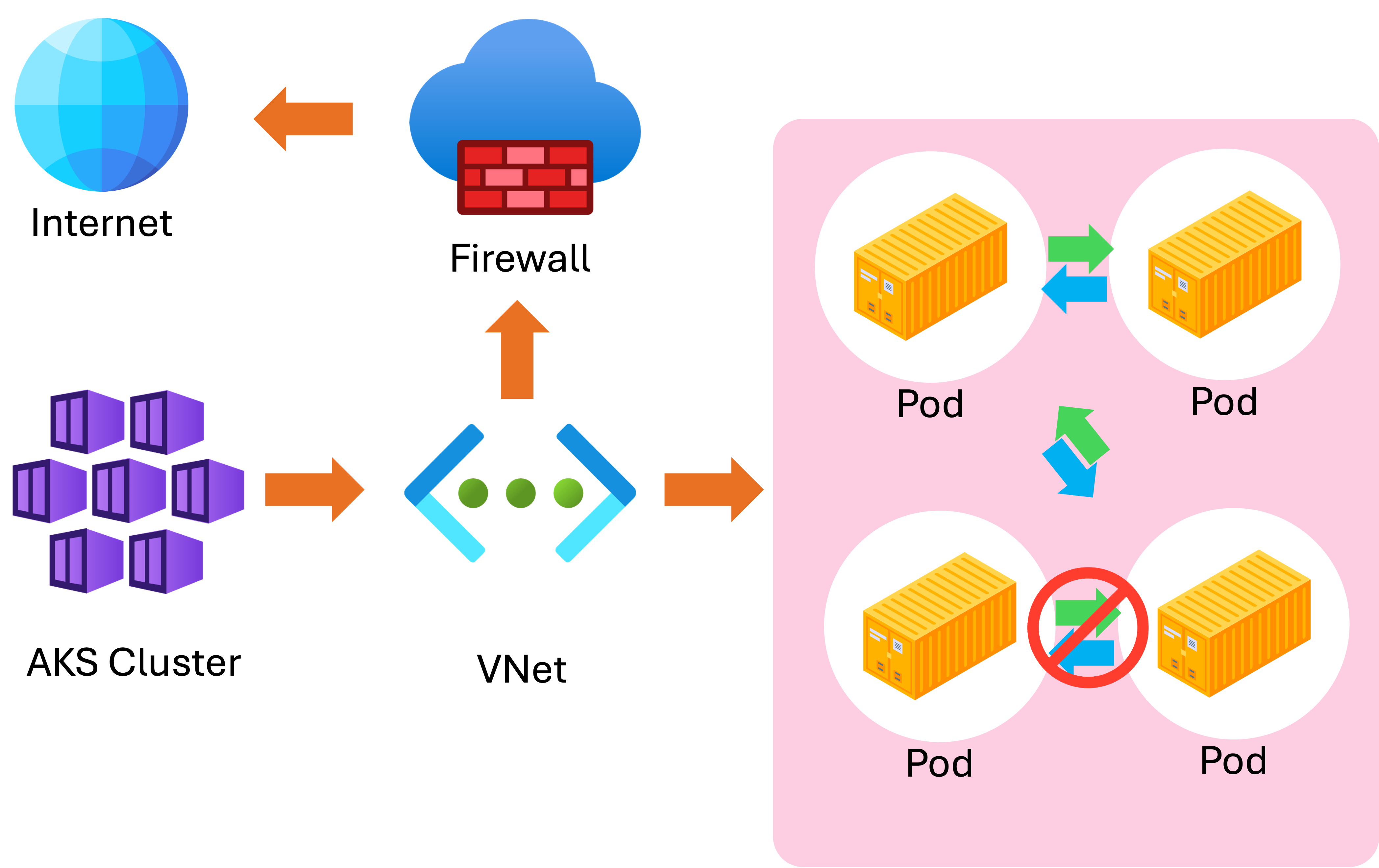
Ingress controllers:
- Configured with TLS certificates
- Secure external traffic
Network policies:
- Define which pods can communicate
- Reduce the attack surface
Image security
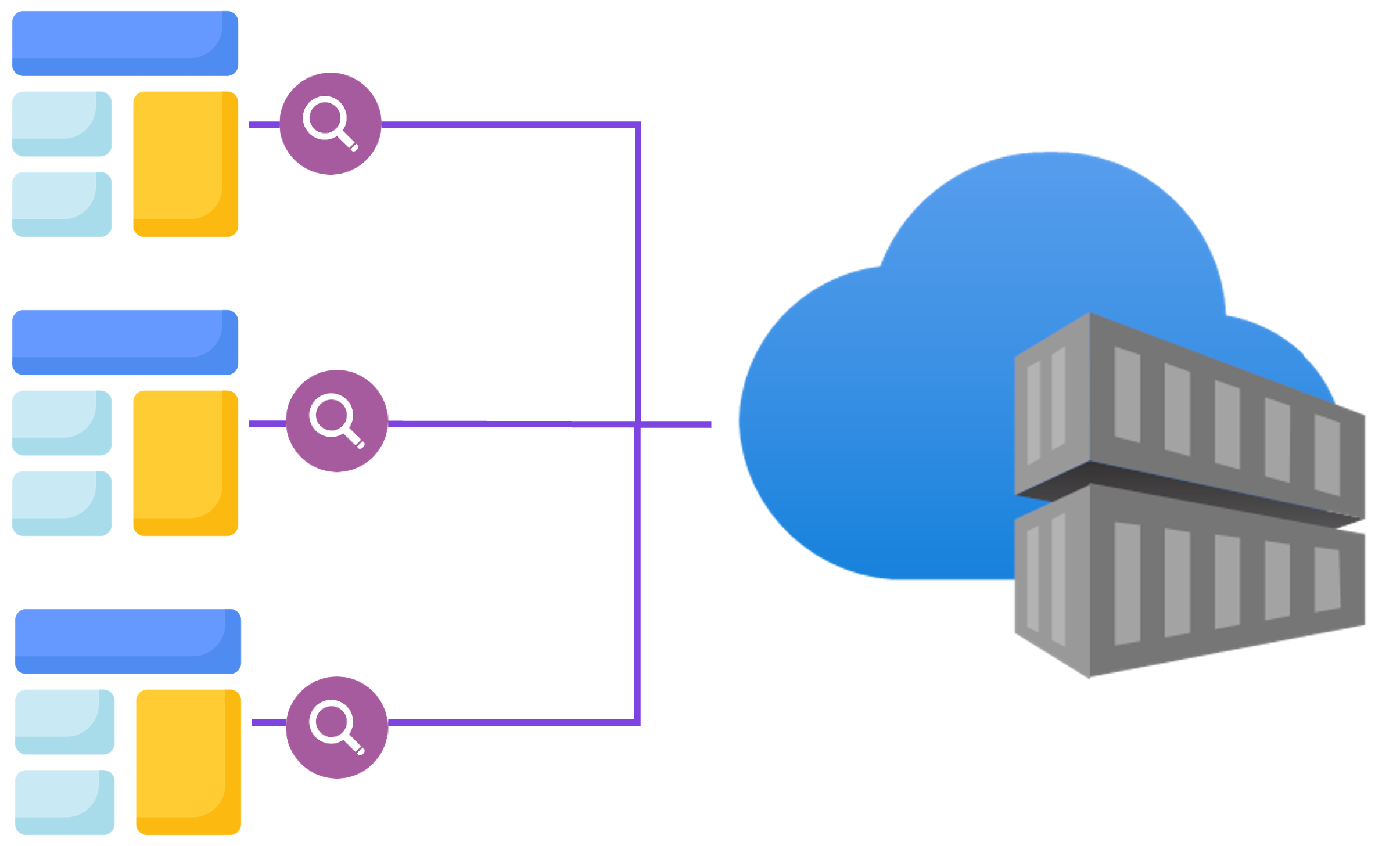
Container images:
- Foundation of workloads
- Must be trusted
Azure Container Registry:
- Supports image scanning
- Detect vulnerabilities before deployment
Image security
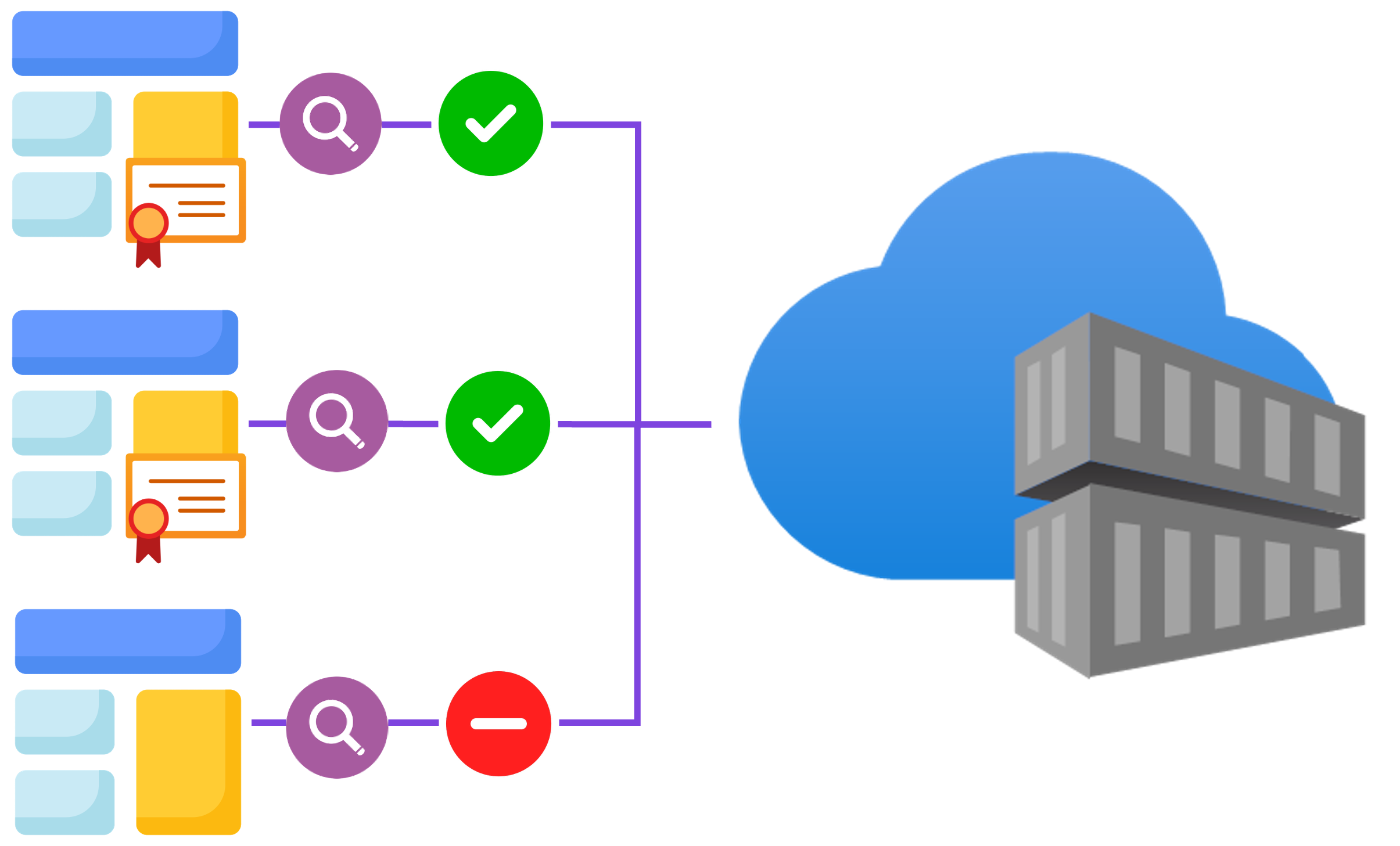
Policies
- Only signed or approved images are allowed in the cluster.
Image security
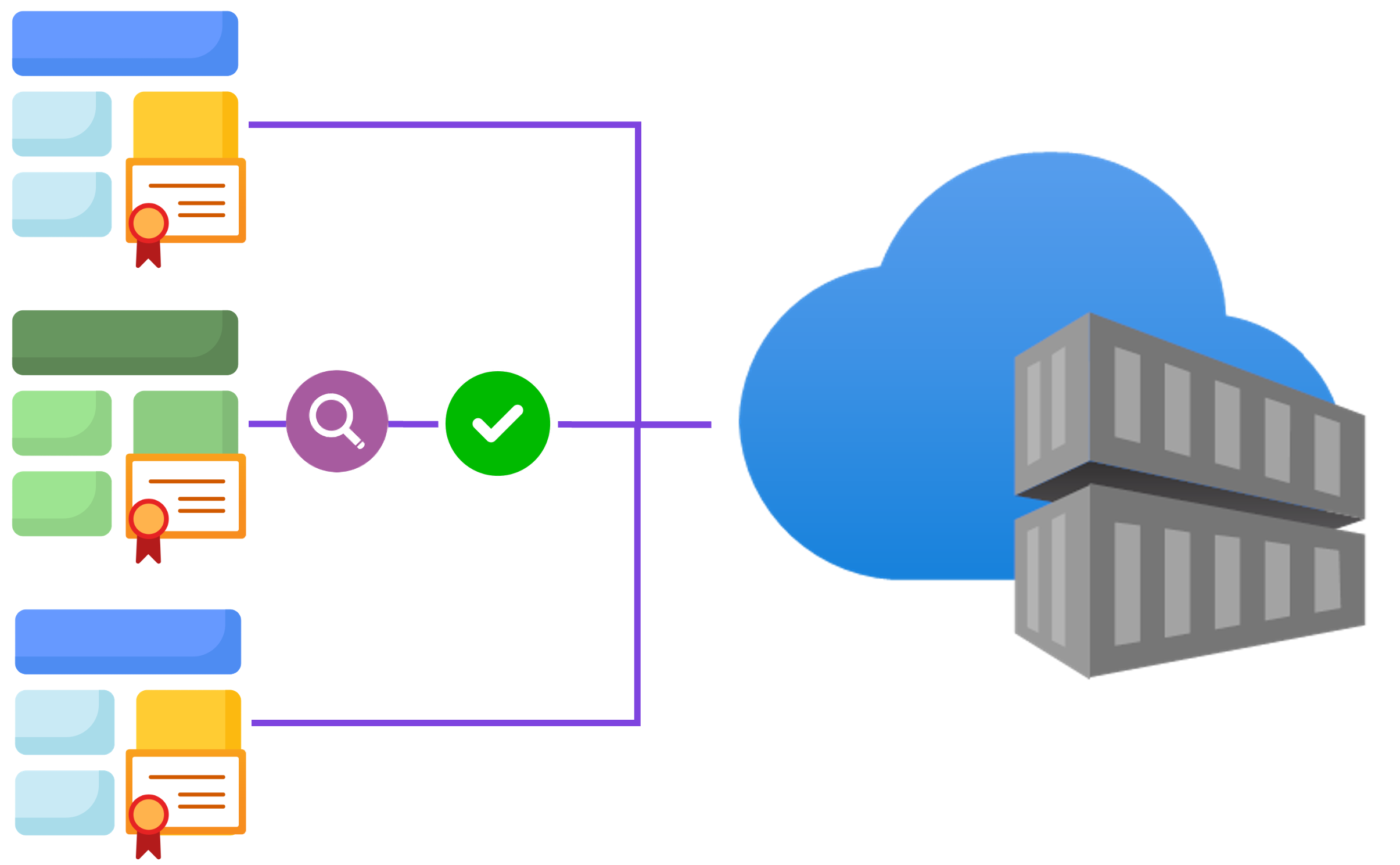
Update base images and apply patches:
- Keep workloads secure
Validating images:
- Prevent compromised software from entering production
Monitoring and compliance
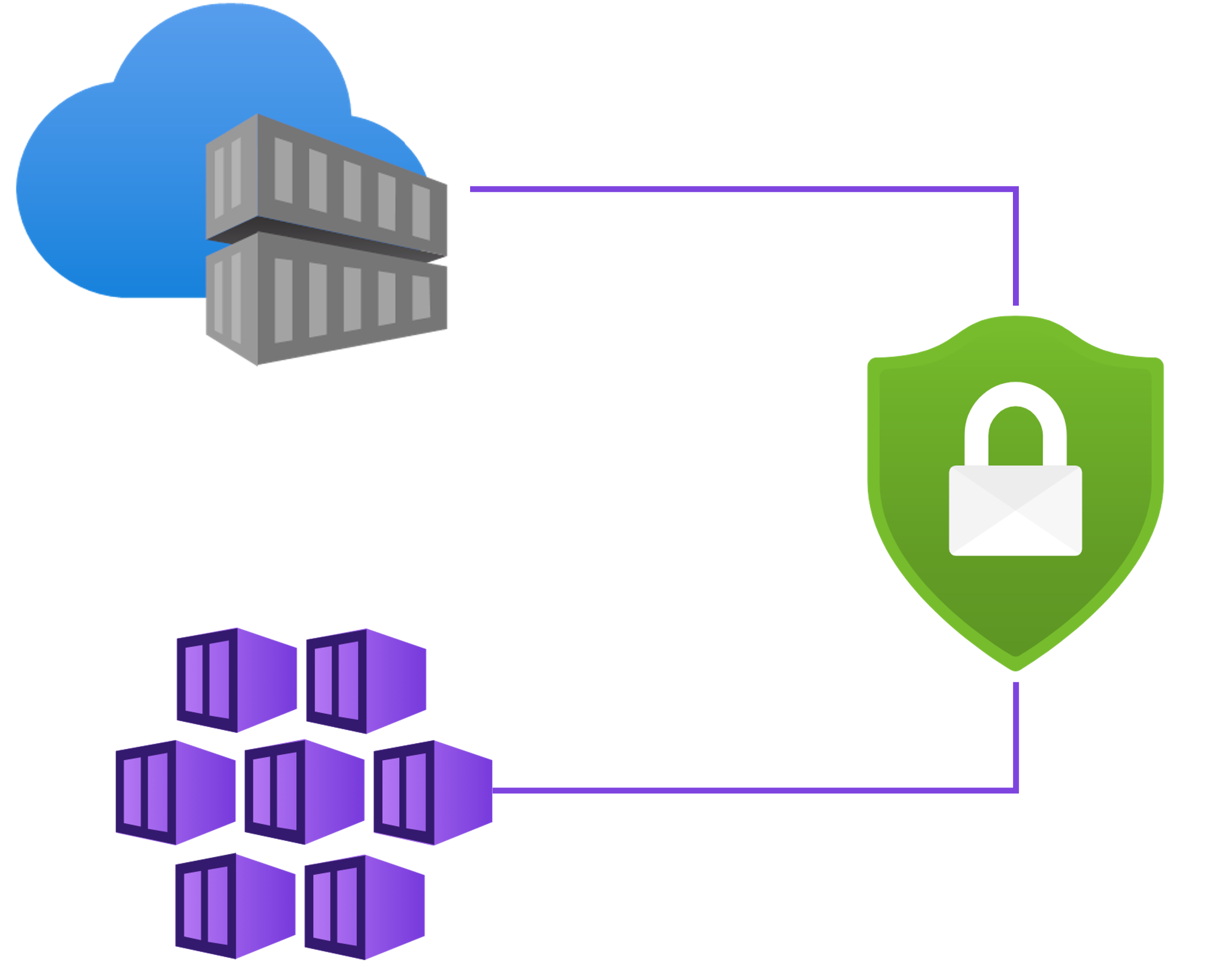
- Continuous monitoring is essential to detect threats.
Azure Defender for Kubernetes
- Runtime protection.
Detecting suspicious activity:
- Privilege escalation
- Abnormal network traffic
Compliance tools:
- Clusters meet organizational or regulatory standards
Recap

Securing applications in AKS:
- Role-Based Access Control
- Secrets management
- Network controls
- Image validation
- Continuous monitoring
Let's practice!
Azure Compute Solutions

